Mission-ready: Standing alongside government and our partners to deliver on the cybersecurity Executive Order
In Blog, EO Blog, Zero Trust, Identity Modernization, Okta, Darktrace, Executive Order, CyberArk, Netskope, Software Supply Chain, FedRAMP, Cloud & App Security, Security Operations, Constellation GovCloud
The Cybersecurity Executive Order (EO) comes at a time when government, businesses, and our way of life are increasingly being disrupted by cyberattacks. It is no wonder that the EO takes an ambitious and comprehensive approach with aggressive timelines on policies, procedures, and technology modernization initiatives. The 7 key sections of the EO reveal two consistent themes: 1) Improve public-private collaboration and 2) Accelerate modernization.
Improve public-private collaboration
We can’t succeed without each other. The EO makes it clear that in order to succeed in defending against today’s threats, the government and the private sector must further strengthen their collaboration. While this public-private partnership has always existed, barriers still exist that create challenges with information-sharing, effective collaboration, and accountability.
The importance of close collaboration became more evident with the recent SolarWinds software supply chain compromise and Microsoft Exchange Server zero-day vulnerabilities. In the SolarWinds attack, it was through the detection of a cybersecurity firm that initially exposed a highly sophisticated campaign that may have begun several months prior to being detected. It was reported days later to government and law enforcement, who then mobilized their incident response.
An even more dangerous vulnerability was discovered just weeks later. With the Microsoft Exchange Server vulnerability potentially impacting hundreds of business systems, the FBI took the unprecedented action of remotely accessing these private servers to remove a web shell backdoor program used by attackers.
The rapid pace of technological innovation and the government’s increasing reliance on technology to deliver on its mission bring to light the need for closer partnership between the private and public sectors.
Accelerate modernization
We need to move faster. When it comes to cybersecurity, speed is vital. The ability to rapidly detect threats and respond to incidents are necessary to keep continuity of business. They are also often the measure of effective security operations. The EO recognizes that for government to keep pace with its adversaries, it needs to accelerate technology modernization.
The EO recommends that government agencies expedite the use of cloud services to quickly and securely move towards a more resilient cybersecurity architecture. Similarly, the EO requires improvements to agencies’ security operations and their ability to identify, detect, and respond to vulnerabilities and incidents.
It is worth noting the focus on zero trust architecture and capabilities of multi-factor authentication (MFA) and data encryption. These capabilities are essential to good cyber hygiene. They help ensure that additional security modernization efforts are built on a strong security foundation. Securing user identities and data security are the cornerstones of an effective zero trust security strategy.
How can Merlin help?
The 7 key sections of the EO reveal logical intersections between the two objectives to improve public-private collaboration and accelerate modernization. As we analyze the EO’s requirements to determine how we can best serve government and industry, we find that these intersections present us with great opportunities for efficiencies and maximize results on our efforts.
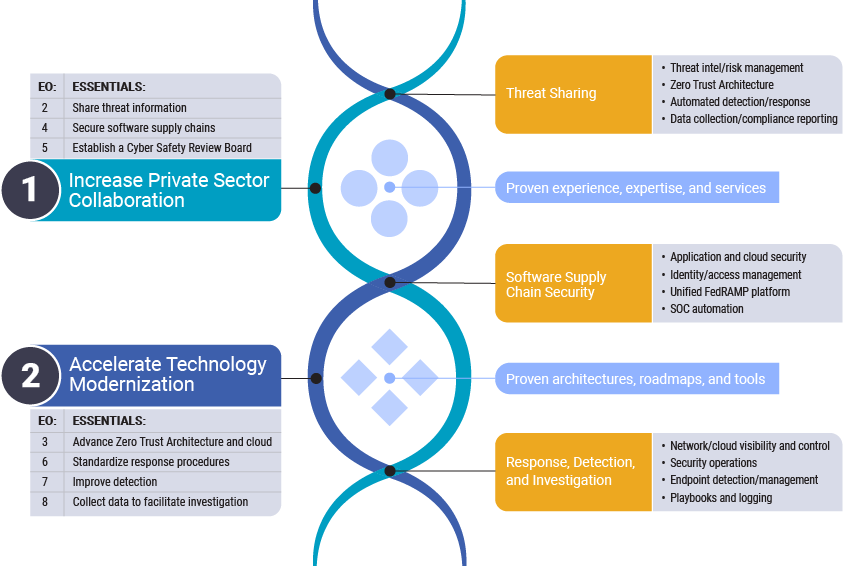
At Merlin, we believe that we are well-positioned at these intersections. With industry-leading partners, innovative solutions, and a secure cloud platform, Merlin can help the government with modernization, secure cloud adoption, and security operations.
Converging at the nexus of security and cloud
The EO requires agencies to prioritize cloud technologies as a faster path towards modernization and zero trust architecture. At Merlin, we offer cloud-based identity security, endpoint security, and data security solutions. Since these solutions are delivered from the cloud, they are quick to deploy and provide rapid time to value. Our identity security solutions enable adaptive MFA and risk-based authentication to all assets on the network. To protect high-value assets, we secure privileged credentials with comprehensive privileged access management.
To secure agencies’ journey to the cloud, we offer cloud security solutions that secure cloud access and protect critical applications across the cloud infrastructure. Cloud has expanded the network perimeter and has become one of the key drivers for the move towards zero trust architecture. At Merlin, we take a holistic approach to zero trust architecture. We apply zero trust security principles to all endpoints, applications, and identities. With our holistic zero trust security, users’ and network access are provided in a least privilege model and continuously verified. Resources are protected with granular-level security with the ability of automated remediation to continuously enforce zero trust principles.
We follow these core tenets to ensure zero trust is applied across the different layers of your infrastructure:
- Identity as a Perimeter
- Least Privilege
- Intrinsic Workload Security
- Micro-segmentation
- Integration & Automation
- Security Analytics
With zero trust security applied throughout the network, agencies can greatly improve the effectiveness of their security operations. The EO requires that agencies implement endpoint detection & response (EDR), logging, and standardized playbooks. At Merlin, we offer solutions for security operations that help our customers apply security analytics and automation to quickly identify and respond to threats and anomalous network activity.
Our cloud-based EDR collects host-based telemetry data for expanded visibility and control of endpoints. Combining threat intelligence data and deep analytics, threat hunting teams can use the cloud-scale data lake to proactively hunt for threats on the network. Security orchestration, automation & response (SOAR) enriches EDR data with additional telemetry data from SIEM, network threat detection, threat intelligence, and other sources, providing better contextual information on incidents and threats.
FedRAMP acceleration
To stay one step ahead of adversaries, agencies must continue to adapt and thrive in a dynamic and evolving threat landscape. Merlin continuously analyzes the cybersecurity landscape for emerging technologies and innovative solutions to help our customers with their toughest cybersecurity challenges. Cloud has proven to be an optimal strategy for cybersecurity companies to deliver their software quickly, and for agencies to consume more easily.
Earlier this year, Merlin Cyber launched Constellation GovCloud, a FedRAMP managed service offering that accelerates our OEM partners’ journey towards FedRAMP authorization. This turnkey, platform-as-a-service built on AWS GovCloud reduces the costs and complexity of FedRAMP by meeting nearly 80 percent of the controls.
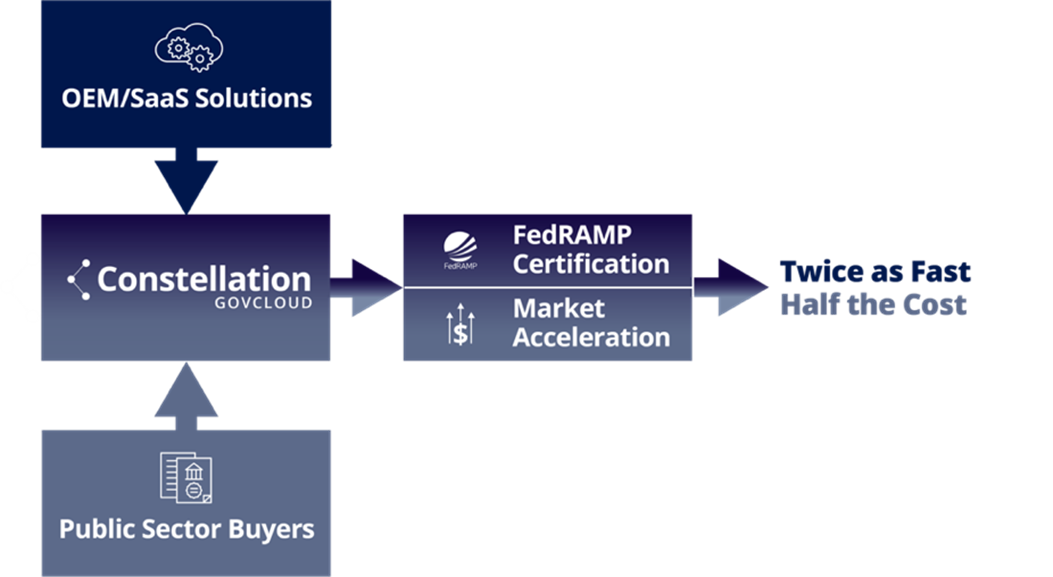
As more stringent requirements are placed on software OEMs to comply with secure software development and testing practices, the OEMs are looking for more effective ways to ensure that they can attest to and demonstrate conformity. Non-compliance can mean removal from government contracting vehicles. Pursuing FedRAMP authorization becomes a viable strategy for companies to demonstrate compliance. Using a FedRAMP authorized cloud service, OEMs can benefit from the baseline security controls and continuous monitoring functions prescribed by FedRAMP for the IaaS and PaaS, thereby demonstrating compliance with the software security requirements in the EO.
Constellation GovCloud benefits our OEM partners with a path towards FedRAMP authorization and the software security compliance that comes along with FedRAMP. At the same time, government benefits from access to a growing number of secure, software-as-a-service cloud solutions.
Winning the battle requires strategy and execution
For nearly 25 years, Merlin has delivered innovative solutions that help our clients reduce security risk and simplify IT operations. We continue to transform our business to ensure that we are constantly delivering value to our clients. Delivering value is in our DNA.
We formed strategic partnerships with the world’s best-in-class cybersecurity brands to provide our clients with solutions they know and trust. Today, we partner with market-leading and trusted cybersecurity vendors such as CyberArk, Darktrace, Netskope, Okta, and Swimlane. We launched Constellation GovCloud to accelerate our OEM partners’ journey towards FedRAMP, and to expand their routes to opportunities in federal. In these unprecedented times for cyber defenders, Merlin stands ready to partner with government and industry to face these challenges.


