Ransomware Protection for the U.S. Government
Empowering Federal Agencies with Proactive, Scalable Cyber Defense Capabilities
Featured Resources:
PROTECTION AND RECOVERY
Access strategic resources designed specifically for immediate ransomware defense and rapid recovery, tailored to the unique needs of federal cybersecurity environments.
CYBERARK EPM DEMO
Stopping Ransomware in Real-Time with Zero Trust & CyberArk EPM
In this demo, we bypass Microsoft Endpoint Detection and Response (EDR), dump credentials, and execute a ransomware attack to show just how quickly your systems can be compromised despite having EDR deployed. Then we flip the script. With CyberArk EPM, we block the attack in real time, eliminate local admin rights, detect lateral movement with decoy accounts, and enforce just-in-time privilege—all powered by AI-driven policy creation.See how our Zero Trust approach works to protect your hosts from threats and eliminate the risk of ransomware.
WATCH NOW
SOLUTION BRIEF
Protecting Against Ransomware with a Comprehensive Cybersecurity
Strategy for Detection and Prevention
The cybersecurity threat landscape is evolving rapidly, and government agencies are at the forefront of protecting critical infrastructure. Ransomware and malware pose significant risks to federal systems, data, and endpoints. As cyber threats grow more sophisticated, federal agencies must implement best practices, actionable strategies, and innovative solutions to secure their attack surfaces and safeguard national security.READ MORE
DATASHEET
Comprehensive Data Security and Resilience with Cryptographic
Vulnerability Management
Cryptography is the underpinning of your data security. Every key, library, certificate, and other cryptographic object represents a vulnerability that attackers can exploit in ransomware, supply chain, and other cyberattacks. By integrating Veeam’s backup and recovery capabilities with InfoSec Global Federal’s cryptographic agility solution, you can ensure continuous data availability while adhering to the highest cryptographic security standards.READ MORE
TRENDS REPORT
Proactive Ransomware Defense and Recovery for Federal Agencies
Veeam’s 2025 ransomware trends report shows actionable steps agencies can take to reduce risk and recover more quickly and successfully from an attack. Overall, 900 respondents were surveyed, including security professionals and IT leaders in 130 US federal government organizations – comprising 82 defense agencies and 48 civilian agencies – that were affected by at least one ransomware attack resulting in encryption or exfiltration in the past year.READ MORE
EXPERT INSIGHTS
Dive deeper into understanding ransomware threats and strengthening your agency's cybersecurity posture.
INSIGHTS
Medusa Ransomware Strikes Again – Are You Protected?
Medusa ransomware is escalating attacks on critical infrastructure. Learn how to defend against this evolving threat with proactive strategies, including vulnerability management, privilege controls, and resilient data recovery.READ MORE
INSIGHTS
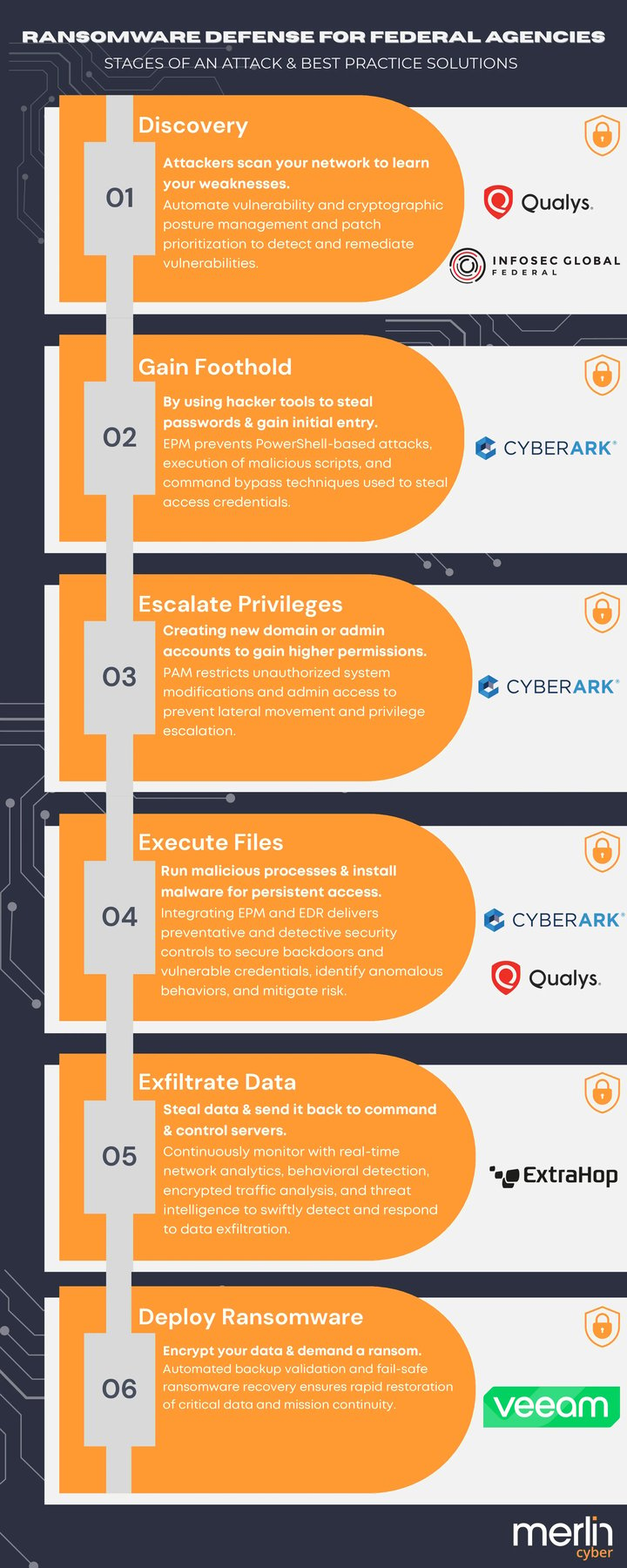
Understanding and Preventing Early Stages of Ransomware Attacks
Explore how early-stage ransomware attacks exploit vulnerabilities through reconnaissance and initial access. Learn proactive measures to detect and prevent these threats before they compromise your systems.READ MORE
INSIGHTS
Mid-Stage Ransomware Protection: Strengthening Security Against Privilege Escalation and Defense Evasion
Delve into strategies to combat mid-stage ransomware tactics like privilege escalation and defense evasion. Discover tools and practices to fortify your defenses during these critical attack phases.READ MORE
INSIGHTS
Advanced Stages of Ransomware: Securing Data and Mitigating Impact
Understand the advanced stages of ransomware attacks, including data exfiltration and system impact. Learn how to secure your data and mitigate damage through effective cybersecurity measures.READ MORE
VISUALIZE THE THREAT
Quickly grasp the critical stages of ransomware attacks and effective mitigation measures through our concise visual guide.
EXPERT PANEL DISCUSSION
Join cybersecurity experts and government panelists as they discuss practical measures for achieving end-to-end resilience against ransomware.
IN PARTNERSHIP WITH



NEED ADDITIONAL SUPPORT?
Have questions or need personalized assistance with ransomware protection for your agency?


.webp?width=666&height=420&name=stopping-ransomware%20(1).webp)








