Zero Trust Made Simple
Accelerating Government Modernization
Merlin helps federal agencies adopt the below core tenets and implement a comprehensive strategy that enables them to achieve full zero trust architecture on their terms. Zero trust is an incremental journey with risk tolerance, speed of execution, and breadth of implementation all key considerations. No matter where an agency is in its path to zero trust, we deliver the solutions needed at the pace and scope desired. With our portfolio of best-in-class security partners and emerging technologies, we can secure every layer of your IT stack, from endpoints to applications, to data and users.
Core Tenets of Zero Trust
To provide cutting-edge solutions, you need to leverage the best minds in the industry.
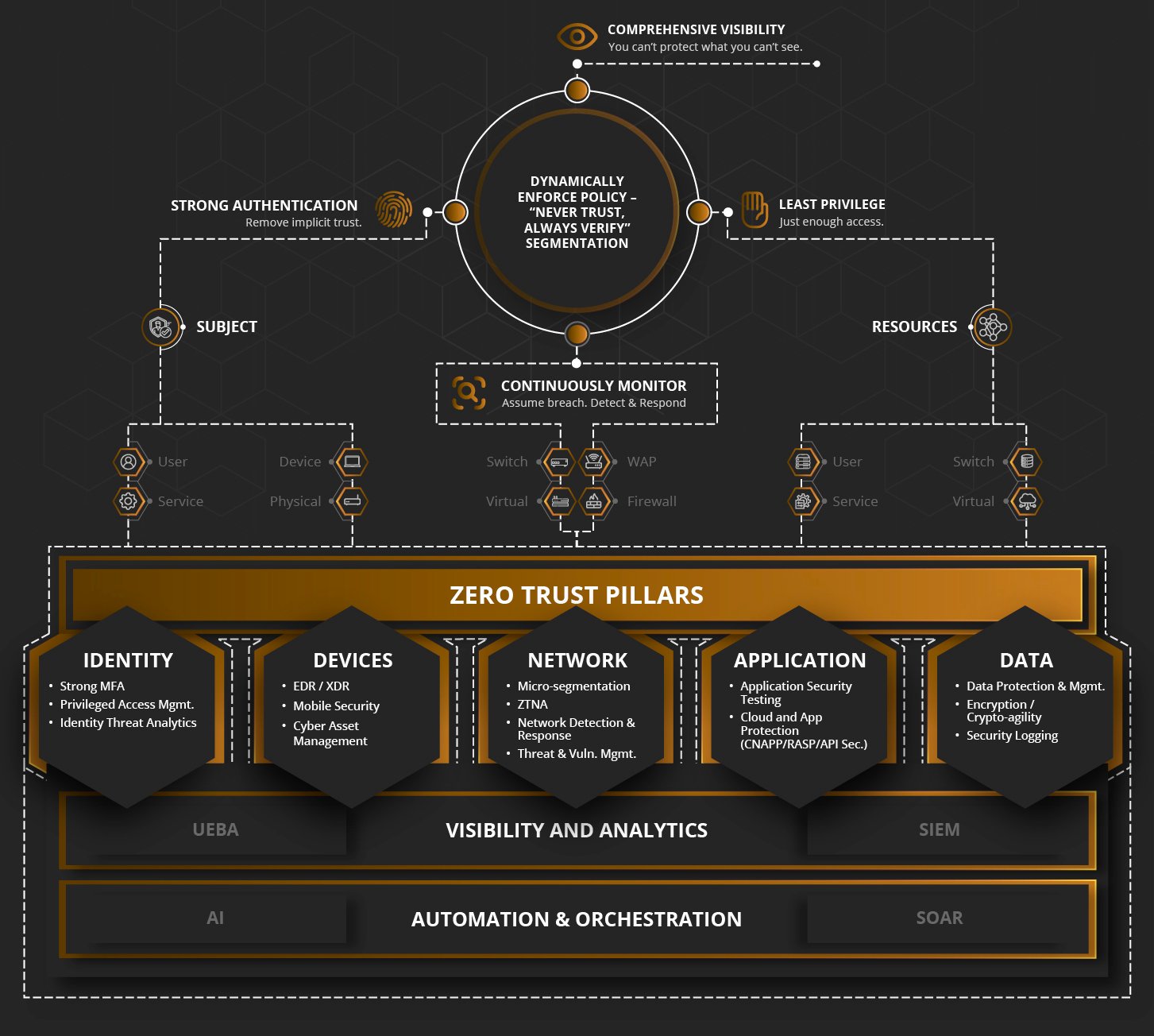
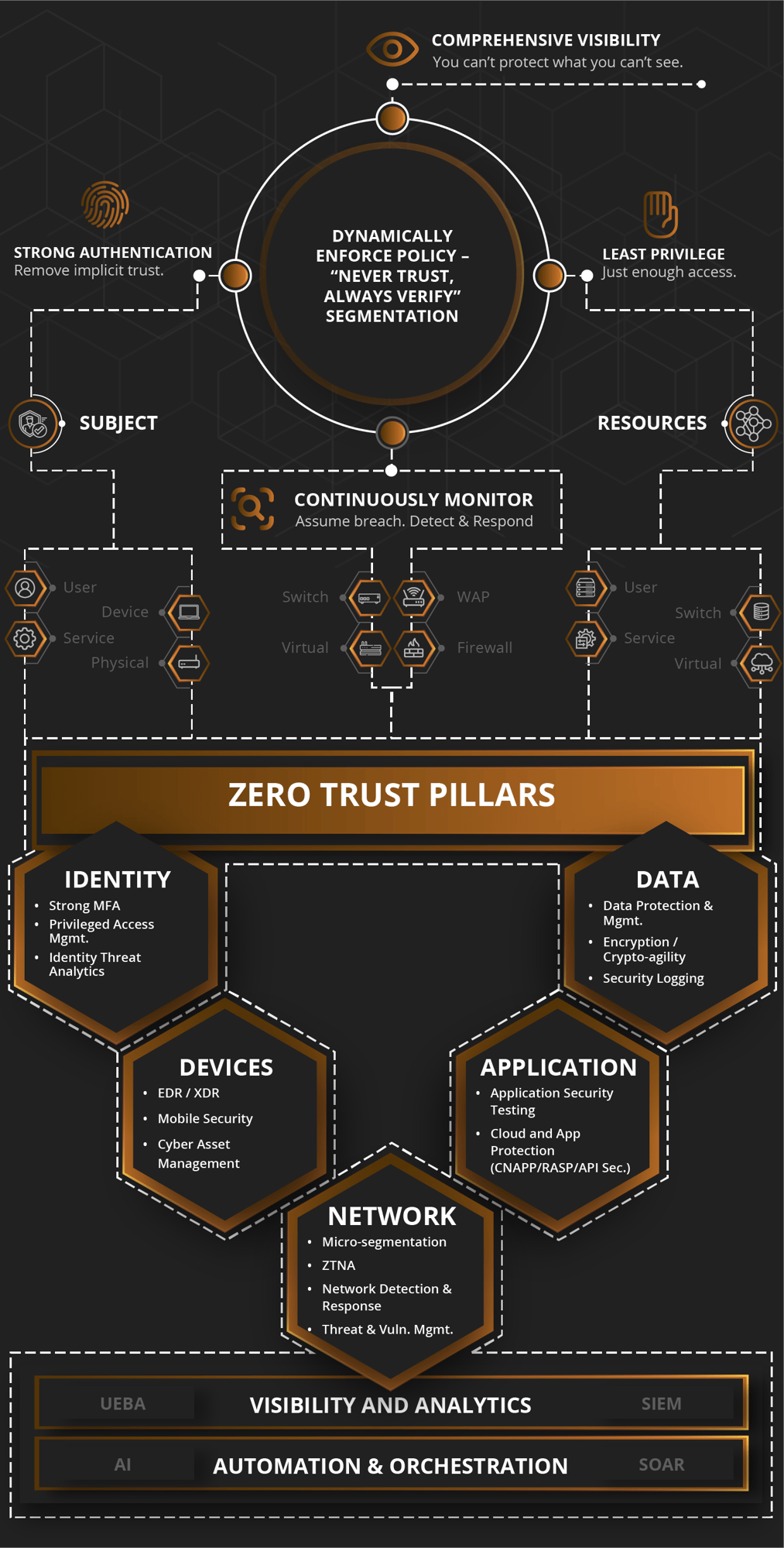
Solutions to Power Your Zero Trust Pillars
Explore solutions that have been fully vetted to help you advance your Zero Trust priorities.
Identity
Identity is at the heart of security. Among top actionable agency identity priorities:
- Employ centralized ID management
- Use strong MFA
- Consider device and ID information
- Eliminate requirements for special characters and password rotation
Devices
How can you protect against sophisticated threats targeting the spectrum of devices? Among the priorities for government agencies:
- Use CDM tools for inventory
- USE EDR tools that meet CISA standards
Network
Government networks are a top target for adversaries -- and for good reason. Among network protection punchlist priorities for government agencies:
- Use encrypted DNS (CISA has supporting service)
- Use HTTPS for all web and API traffic
- Develop a Zero Trust Architecture plan
Apps/Workload
Government networks are a top target for adversaries -- and for good reason. Among network protection punchlist priorities for government agencies:
- Use encrypted DNS (CISA has supporting service)
- Use HTTPS for all web and API traffic
- Develop a Zero Trust Architecture plan
Data
Government holds the keys to highly sensitive data which is dispersed throughout a hybrid enterprise. Among data security punchlist priorities for government agencies:
- Automate data categorization and security
- Audit access to any encrypted data in the cloud
- Implement event logging per M-21-31
Visibility and Analytics
Agencies need comprehensive visibility across the enterprise in order to prioritize risk and take timely mitigation actions. Among the punchlist of priorities for agencies:
- Collect and process all logs, including network, data, application, device, and user logs and make those available to the appropriate CNDSP or SOC
Automation and Orchestration
Agencies are embracing orchestration and automation to optimize operational efficiency and mitigate risk. Among the punchlist priorities for agencies:
- Conduct task automation analysis to identify repetitive, predictable cybersecurity tasks suitable for techniques like RPA
- Analyze Policy Enforcement Points (PEP) and Policy Decision Points (PDP) for automation


























