Quantum Threat Mitigation
Mitigate Risk to Vulnerable Cryptographic Systems
The Next Real Threat to Your Sensitive information is on a Quantum Level
Federal systems and data are currently protected using encryption methods that must keep pace with the rapid development of quantum computing. Some forms of cryptography will likely be able to be cracked with quantum computers. The stakes couldn't be higher -- this could bring our nation's most critical systems to a grinding halt and relinquish sensitive data and secrets to adversaries.
Agencies have been issued requirements to immediately begin their migration journey to post-quantum readiness. From discovery to dynamic response, we empower you and your mission with crypto-agility.
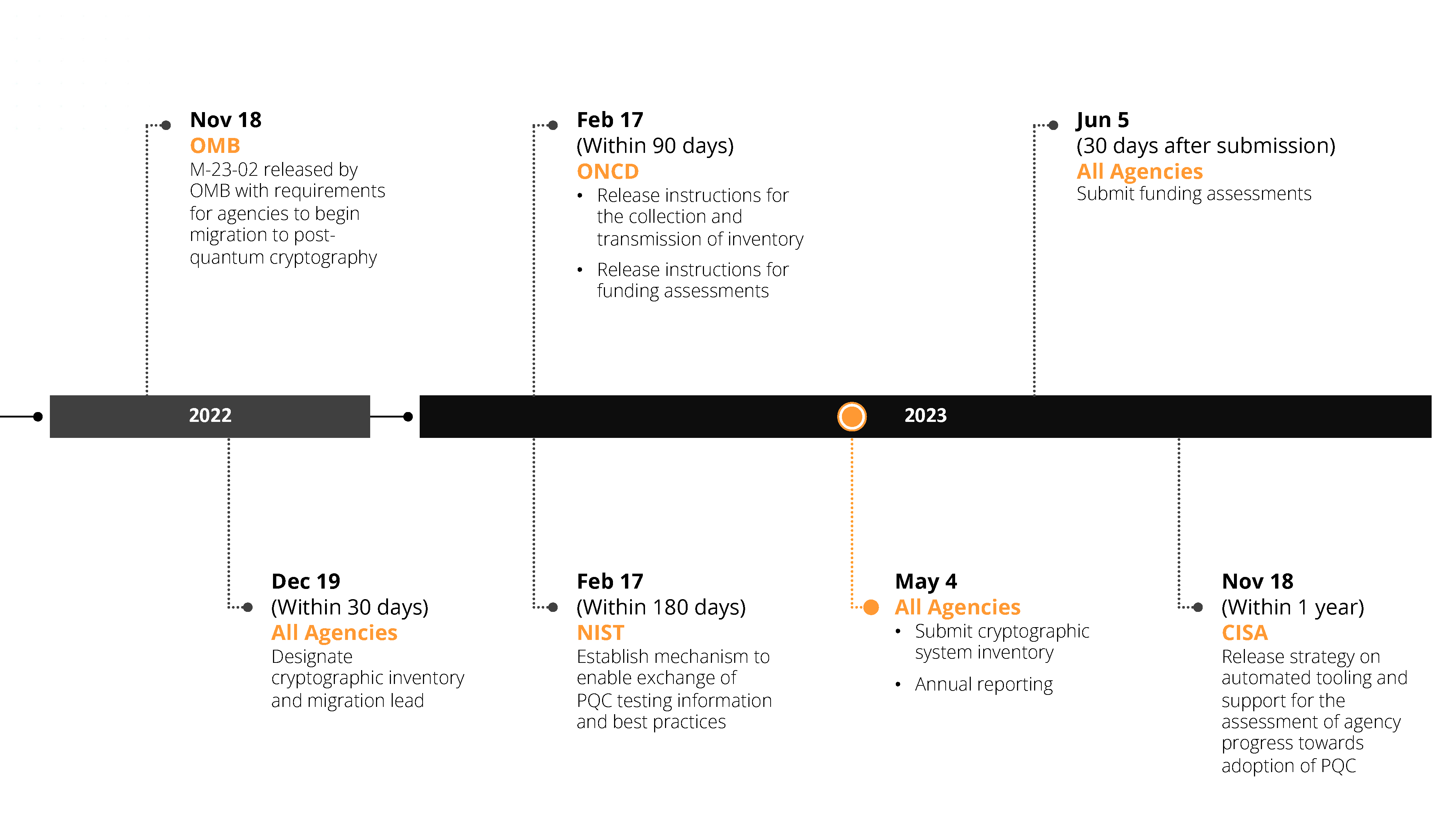
Requirements Timeline
Prepare Your Systems for Quantum Threats
OMB issued a memo (M-23-02) requiring all agencies to submit cryptographic system inventory by May 4, 2023 in compliance with National Security Memorandum 10 (NSM-10) on Promoting United States Leadership in Quantum Computing While Mitigating Risk to Vulnerable Cryptographic Systems. Immediate action must be taken – we can help.
Take Action Now
Organizations with any data/assets of value will need to exercise due diligence towards fully understanding and mitigating risks to vulnerable systems. The direction provided by M-23-02 puts into action the guidance of NSM-10 and also aligns with the zero trust strategy put forth by EO 14028.
In the immediate term, we can help you meet your cryptographic inventory requirements with very little lift and disruption. We also help you meet ongoing requirements as your agency matures its post-quantum cryptography by providing a PQC strategy, execution plan, and continuous reporting to meet annual reporting requirements.
- Discovery and inventory all forms of cryptography
- Cryptographic analytics for resiliency and remediation
- Cryptographic governance, reporting, and compliance
- Cryptographic sovereignty and post-quantum agility
Learn More About Post-Quantum Cryptography
Get Post-Quantum Ready: Let's Talk
Merlin’s team is available to provide valuable information and help you determine what next steps you need to take on your path to Post-Quantum readiness and protection.





