Unmasking the Attacks & Fortifying Defenses
Introduction
Recently, I came across a hair-raising account from an organization actively engaged in threat hunting. During this high-stakes activity, they stumbled upon an ongoing incident that immediately sent their adrenaline soaring. With hearts pounding and the urgency of the situation weighing heavily on their minds, the team made a snap decision to remote log into the compromised device using a privileged account. This hasty action, unfortunately, played right into the hands of the attacker. This real-life episode underlines the stealth and danger posed by sophisticated attacks like the silver ticket attacks in the realm of cybersecurity.
In the intricate dance of cyber defense, where the margin for error is razor-thin, understanding and countering threats require not only vigilance but also precise knowledge and the right set of tools. These attacks are very sophisticated threats that require a calculated and informed approach for detection and prevention.
This article aims to shed light on silver ticket attacks and illustrates how combining Elastic Security, Swimlane SOAR, and CyberArk PAM can offer robust protection against these devastating threats that traditional defenses, like Multi-Factor Authentication (MFA), won’t protect against.
A Brief Exploration of Silver Ticket Attacks
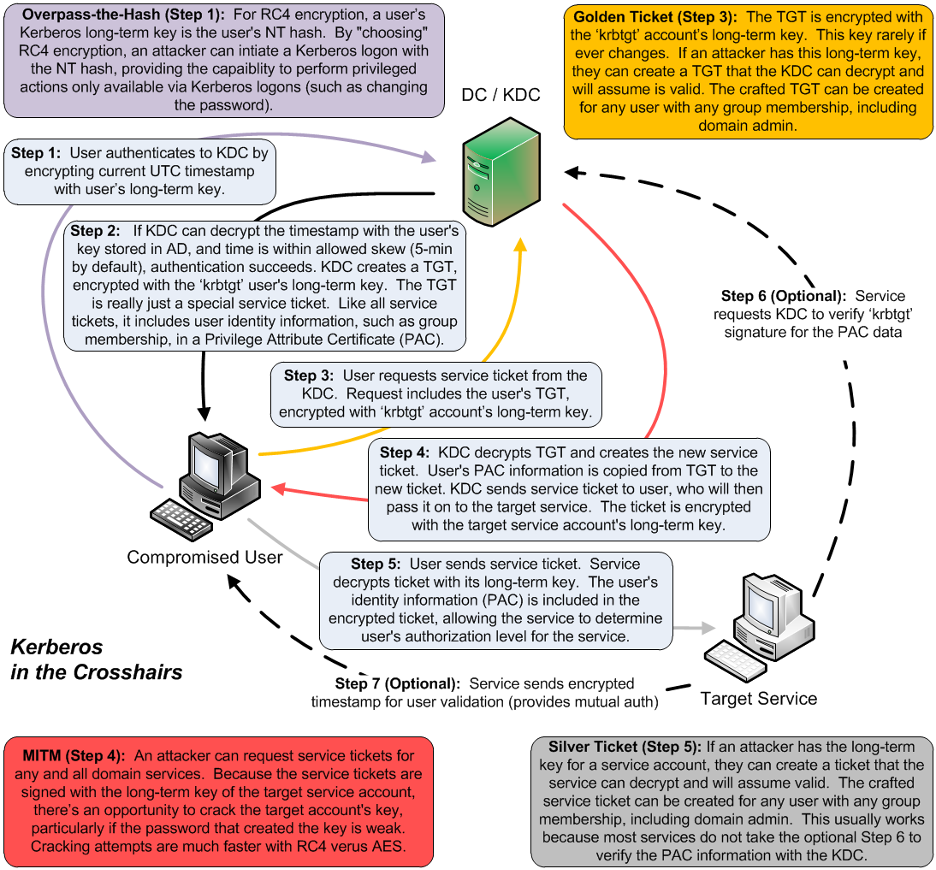
Silver ticket attacks focus on exploiting the Kerberos authentication protocol, specifically targeting the service tickets generated during the Kerberos ticket-granting process. In a typical scenario:
- Attackers Gain Unauthorized Access: They exploit system vulnerabilities or use phishing techniques to initiate the attack.
- Service Key Extraction: The attackers then extract service keys related to specific services on target servers through various tools designed for this purpose.
- Forging Silver Tickets: With the service keys in hand, attackers craft silver tickets, granting them unauthorized and undetected access to specified services.
- Malicious Activities: These tickets allow attackers to exfiltrate data, execute commands, or perform other malicious activities without raising alarms.
Why MFA Isn’t a Silver Bullet
While Multi-Factor Authentication (MFA) is crucial for enhancing security, it isn't infallible, especially against silver ticket attacks. These attacks sidestep user credentials, rendering MFA ineffective as attackers exploit service-level vulnerabilities instead of user accounts. Additionally, silver ticket attacks can bypass other security measures, such as firewalls and intrusion detection systems, as they exploit vulnerabilities in the Kerberos protocol itself, which is used for authentication throughout the network.
Elastic Security’s Role
Elastic Security stands as a pillar in monitoring for silver ticket attacks, offering SIEM, endpoint protection and threat hunting capabilities. By setting up rules that scrutinize user logins, Kerberos ticket timestamps, source IP addresses and unusual access patterns, Elastic Security effectively generates alerts for suspicious activities signaling potential silver ticket attacks.
Swimlane SOAR: Automating Response
Swimlane SOAR complements detection by automating responses to silver ticket alerts. You can configure it to disable compromised user accounts, notify affected users, investigate the attack source, and execute other mitigation steps swiftly and efficiently.
CyberArk PAM: Privilege Management
Despite MFA's limitations, incorporating CyberArk PAM helps control access to privileged accounts and prevent attackers from escalating privileges using stolen credentials. Session monitoring and recording features within CyberArk PAM further empower your team to identify and investigate suspicious activities indicative of silver ticket attacks
Synergizing Technologies
Integrating the function of Elastic Security, Swimlane SOAR, and CyberArk PAM to create a resilient defense against sophisticated attacks is a specialty of Merlin Cyber. Our cybersecurity firm understands the intricacies of combining these tools effectively to build a holistic cyber warfare defense strategy. With expert knowledge and skills, Merlin Cyber recommends this powerful trio, that when correctly integrated and configured, provides a comprehensive and proactive approach to network security, encompassing detection, response, and prevention against threats like silver ticket attacks.
Practical Tips for Implementation
Fine-Tune Detection Rules
In Elastic Security, establish and continuously refine a diverse set of detection rules specific to Kerberos protocol anomalies and silver ticket characteristics, minimizing the risk of false positives and negatives.
System Patching and Hardening
Regularly apply updates and patches to your systems to close known vulnerabilities that attackers might exploit to gain initial access. Additionally, implement security best practices to harden your servers, particularly those running Kerberos and related services is key. Don’t set services to utilize user accounts. Opt instead to use a managed service account or group managed service accounts that enforce rotating strong passwords every 30 days. Additionally, configure PAC validation for all TGS requests to validate the tickets presented are valid.
Monitor Service Account Activity
Pay meticulous attention to the activities associated with service accounts. Look for unusual access patterns, login locations, or privilege escalations, which might be indicative of silver ticket attacks in progress.
Educate and Train Your Team
Ensure that your cybersecurity personnel understand the nuances and indicators of silver ticket attacks. Conduct regular training sessions and simulation exercises to keep their knowledge and response strategies sharp.
Leverage Automated Responses Wisely
When configuring Swimlane SOAR, carefully define the automated responses to silver ticket alerts. These might include disabling compromised accounts, notifying affected users, or initiating further investigations. However, always consider the balance between swift response and the risk of disrupting normal operations.
Engage Experts
Consider engaging with cybersecurity experts and consultants like Merlin Cyber who specialize in defending against sophisticated attacks, including silver ticket attacks. Their expertise can provide valuable insight and support in enhancing your defense mechanisms.
Conclusion
Addressing and mitigating the risks posed by silver ticket attacks is a complex task requiring both in-depth knowledge and the right set of technological tools. Merlin Cyber stands out as a reliable partner in this endeavor, offering skilled Blue Team engineering consulting and access to the top cybersecurity vendors for protecting your systems. With a team of dedicated professionals, Merlin Cyber is committed to helping you effectively detect, respond to, and prevent sophisticated and stealthy threats. For a robust defense strategy and peace of mind in the face of evolving cyber threats, Merlin Cyber is here to assist.
Additional Reading:



