
How are you defending against network device vulnerabilities?
Shut Down Attacks with Proactive Router, Switch and Firewall Security
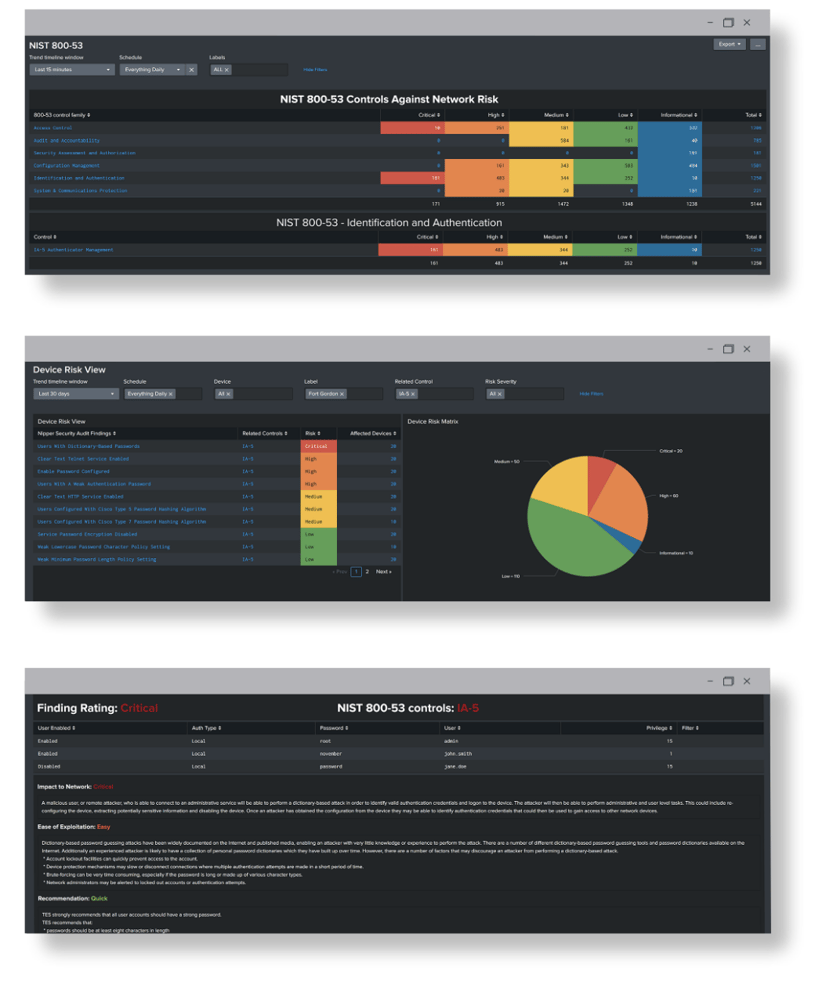
Titania's Nipper Resilience is a solution uniquely positioned to help federal agencies stop adversaries exploit vulnerabilities and establish footholds, take down networks and disrupt mission operations.
Titania is a global leader in network infrastructure security and compliance, providing a powerful platform through which to continuously detect, analyze and remediate configuration changes in firewalls, switches and routers that would otherwise leave agency networks vulnerable to APTs and other threat actors.
How Nipper Resilience Helps Agencies Defend Against Nation-State Attacks From the Inside-Out
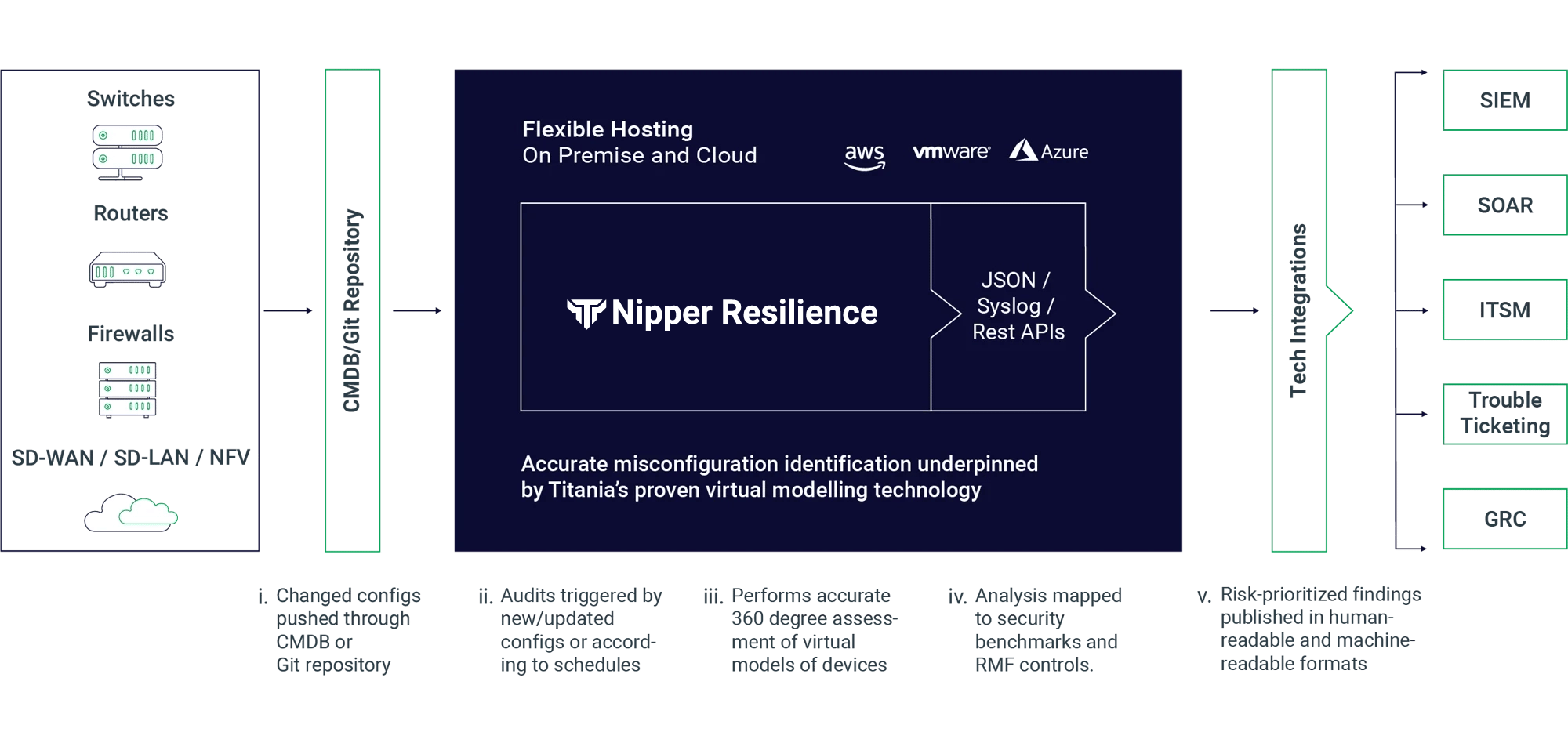
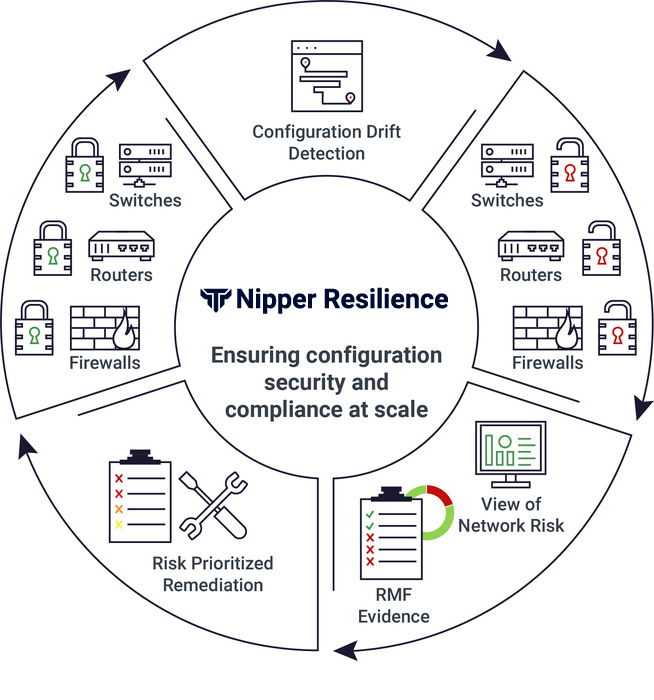
Detecting configuration changes proactively, Nipper Resilience automatically triggers checks to determine whether devices remain secure. And when a configuration has drifted away from the secure state, the solution automatically assesses the exploitability, impact of exploitation and ease of fix -- as well as the command line detail needed to mitigate the risk.
The agency's vulnerabilities can then be viewed in a MITRE ATT&CK dashboard* to show SOCs which would most likely be targeted by threat actors operating right now. Automatically prioritizing these critical risks, Nipper Resilience then helps NOC teams target remediation workflows to secure devices, assure effective network segmentation and shut down attacks.
*Nipper Resilience also offers a range of compliance lenses through which to analyze and prioritize risks, including DISA STIGs, NIST 800-53 and PCI DSS 4.0 dashboards.
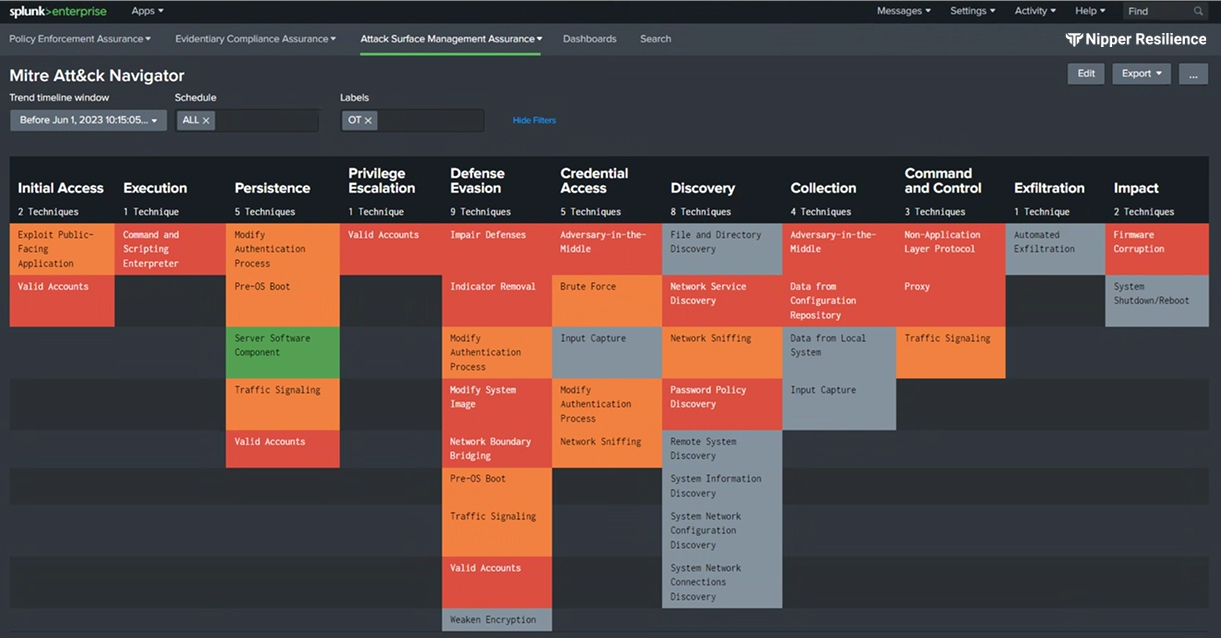
MITRE ATT&CK Dashboard in Nipper Resilience showing which TTPs the network is most vulnerable to, at the point of assessment
Nipper Resilience reports are also transformative in helping threat hunting teams determine where attacks will have proliferated based on historic network segmentation and device vulnerability at the time of the first indicator of compromise.
Titania Can Help Your Agency:
- Proactively manage configuration drift in firewalls, switches and routers
- Improve mean time to remediate critical network risks
- Assure Zero Trust segmentation
- Stop ransomware proliferation
- Guide threat hunting and inform incident response
- Evidence continuous compliance with RMFs
Why Titania?
Supporting CNI security and compliance missions for more than 10 years, Titania solutions’ unrivaled accuracy is achieved by virtually modeling a device configuration as a single entity to consider interdependencies in the network. This is proven to detect critical misconfigurations that would go undetected by other solutions. As well as reducing audit times by more than 80%, reducing the MTTD/R critical network vulnerabilities, and saving thousands of SOC and NOC labor hours per year. See what Titania can do for your mission...
Key Features & Benefits
- Architected for the enterprise
A horizontally scalable, agent less web-based application, Nipper Resilience is designed to support internal and external use cases via multi-tenanted deployments.
- Flexible deployment
Can be deployed either on-premise with an OVA, enabling deployment in offline environments, or on a virtual private cloud with an AMI. - Accessible and integrated
Accessible through modern web browsers and provides Rest APIs and JSON outputs for integration with trusted 2FA, SIEM, SOAR, GRC and ITSM/trouble-ticketing solutions. - Supports all major device manufacturers
Including Cisco, Palo Alto, Juniper, F5, Check Point, Engage, Arista and Aruba - Passive
Solution does not require access to devices, but instead connects to a CMDB or Git repository so the application remains stateless and presents a minimal attack surface. - Inherits config repository segmentation data
Automatically inherits the labels set up in the repository for analysis. Only configuration identifiers are passed to third-party solutions to ensure device locations remain obfuscated, as required. - Customizable audit scheduling by network segment
Schedule audits according to device labels such as network criticality, geographic location, manufacturer, device type, etc. - Configurable check parameters
Detailed check descriptions and configurable parameters help ensure network infrastructure assessments reflect organizational policies and risk profile. - Agnostic data pipeline
Risk-prioritized findings are provided in both human-readable and machine-readable formats, enabling integrations.







