DevSecOps
Incorporate security into your rapid development workflow
Develop Better Code Faster, Without Compromising Security
The accelerated pace of digital transformation demands rapid development of business applications. Tacking on security at the end of dev cycles by a separate security team was manageable when applications were released a few times a year. With Agile and DevOps practices reducing dev cycles to weeks and even days, retrofitting security into applications creates unacceptable and expensive delays. It’s time to take a modern approach to software development by shifting security left in the CI/CD pipeline and empowering developers to fix vulnerabilities as they code.
Speed of delivery doesn’t need to be compromised by adding security to the mix. Merlin offers disruptive solutions that accelerate dev cycles while removing the friction legacy approaches create between development, security, and operations teams.
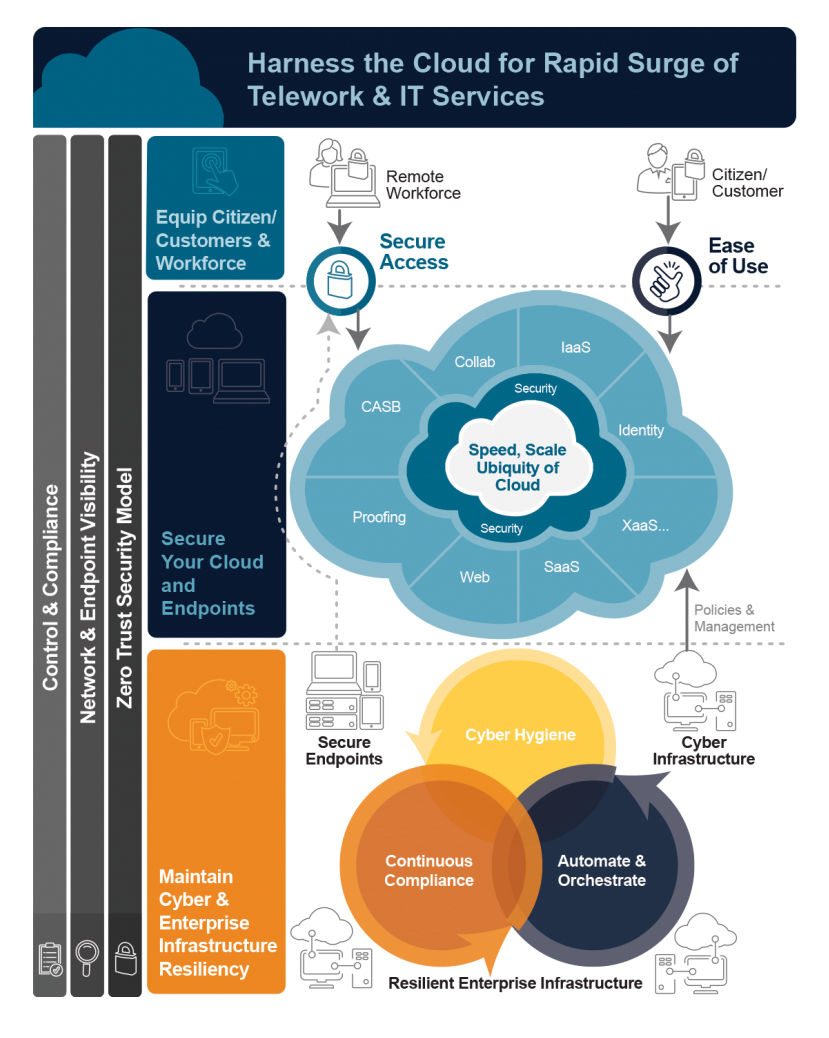
Support remote workers, wherever they may be
A shift in workforce arrangements means that organizations must secure remote workers and anyone else who requires access. That is a challenge as the recent rapid demand for such arrangements has stressed legacy remote access systems, which are not designed to secure remote workers, protect endpoints, or remotely access applications. But by implementing a zero trust architecture, enterprises can adapt to heavily remote workforces, support existing infrastructures, and enhance security all at once.
Merlin helps organizations design secure support for a variety of needs and ensures remote worker identities are properly authenticated. We do this while utilizing current VPNs and existing infrastructure, meaning there’s no need to rip and replace legacy systems. See how we can help your organization secure remote workers with solutions that solve immediate needs today while enabling you to scale and adapt for the future.