OT/IT Convergence
Secure IT and OT environments in the era of convergence
Different But Inherently Linked Security Challenges
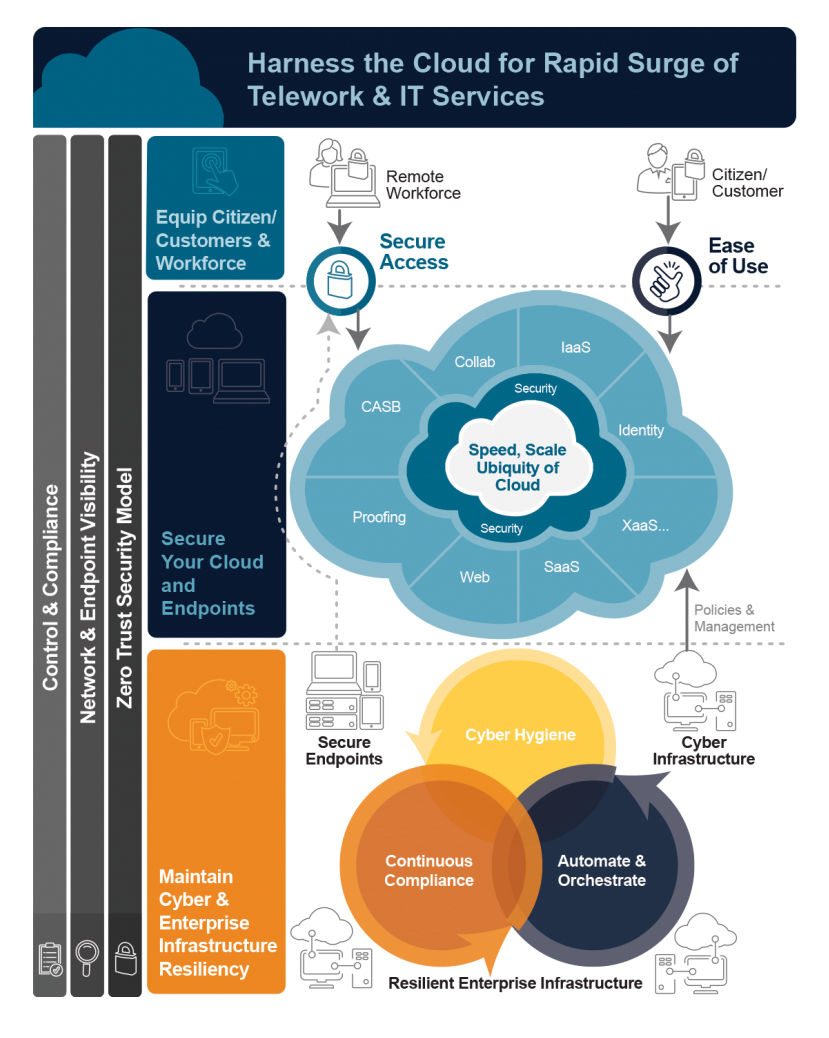
Government networks are evolving to meet today’s missions. We are now in the era of IT and operational technology (OT) convergence, where legacy OT systems are increasingly being updated to include IoT devices and connect to IT systems. The result is an expanded attack surface as previously isolated OT systems, once relatively immune to cyberattacks, are now internet-accessible and high-value targets for threat actors.
Mission success depends on secure operations, but IT, OT, and IoT assets all have different characteristics, communications, behaviors -- and unique security challenges. It’s time to take defense up a notch and reduce cyber risk with a proactive approach designed to secure your complex ecosystem of IT, OT, and IoT assets.
Merlin’s holistic cybersecurity solutions combine best-in-class and visionary capabilities with AI-powered analysis to provide comprehensive visibility, protection, and control within a zero trust security framework.
Support remote workers, wherever they may be
A shift in workforce arrangements means that organizations must secure remote workers and anyone else who requires access. That is a challenge as the recent rapid demand for such arrangements has stressed legacy remote access systems, which are not designed to secure remote workers, protect endpoints, or remotely access applications. But by implementing a zero trust architecture, enterprises can adapt to heavily remote workforces, support existing infrastructures, and enhance security all at once.
Merlin helps organizations design secure support for a variety of needs and ensures remote worker identities are properly authenticated. We do this while utilizing current VPNs and existing infrastructure, meaning there’s no need to rip and replace legacy systems. See how we can help your organization secure remote workers with solutions that solve immediate needs today while enabling you to scale and adapt for the future.