Remote Work
Enable workers anywhere and everywhere with secure, convenient access
Forget VPN, Here's Zero Trust
The coronavirus pandemic dramatically altered the work landscape, forcing thousands of employees to remotely access job-critical tools, applications, and data and placing unparalleled demand on VPNs to provide secure, encrypted connections. With a new, post-pandemic future emerging, it’s time to move beyond legacy perimeters and VPNs and adopt an identity-based approach to security.
Unprecedented change requires modern solutions. A comprehensive zero trust strategy is the most effective way to meet the recently shifted security needs of the public sector. See how we can help your organization secure remote workers with solutions that solve immediate needs today while enabling you to scale and adapt for the future.
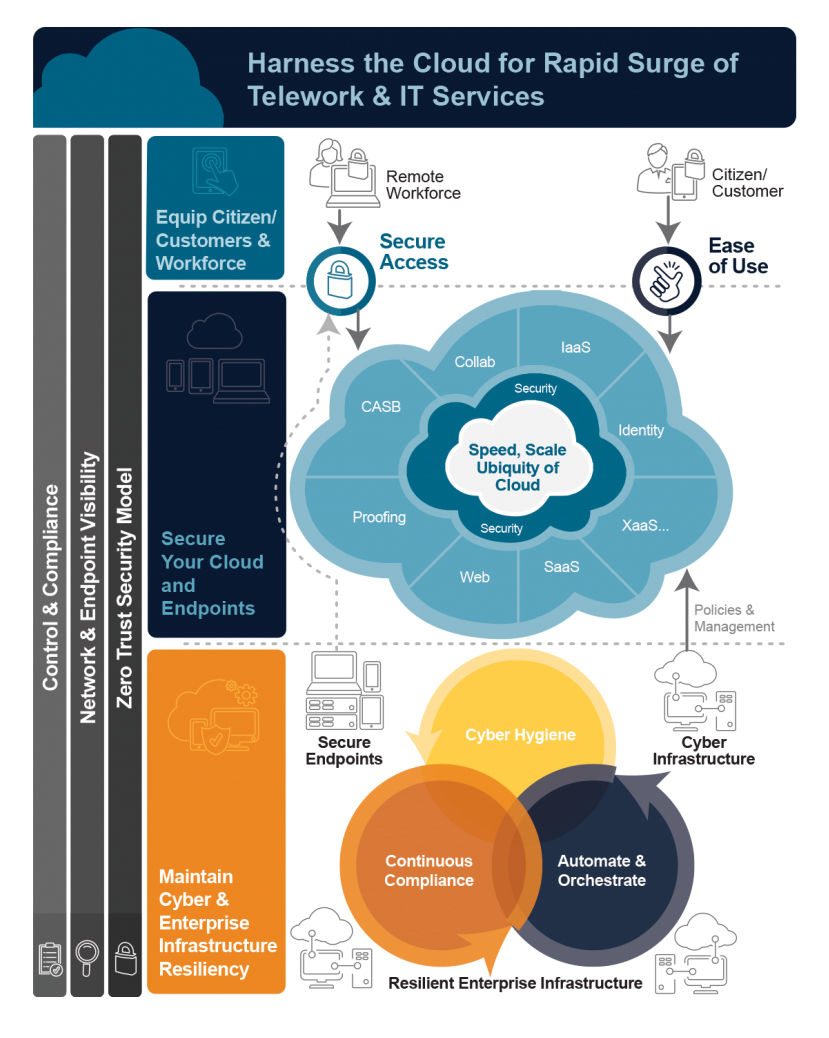
Support remote workers, wherever they may be
A shift in workforce arrangements means that organizations must secure remote workers and anyone else who requires access. That is a challenge as the recent rapid demand for such arrangements has stressed legacy remote access systems, which are not designed to secure remote workers, protect endpoints, or remotely access applications. But by implementing a zero trust architecture, enterprises can adapt to heavily remote workforces, support existing infrastructures, and enhance security all at once.
Merlin helps organizations design secure support for a variety of needs and ensures remote worker identities are properly authenticated. We do this while utilizing current VPNs and existing infrastructure, meaning there’s no need to rip and replace legacy systems. See how we can help your organization secure remote workers with solutions that solve immediate needs today while enabling you to scale and adapt for the future.