
Secure Remote Access with Zero Trust
The most resilient and scalable way for agencies to support mass telework
Almost half of federal government employees engaged in some form of situational telework in 2018, with drastically varying levels of remote access infrastructure between agencies. The COVID-19 public health emergency has exponentially increased the number of teleworkers and pushed agency networks and remote systems to capacity. By implementing a zero trust architecture, federal agencies can adapt to heavily remote workforces, support existing infrastructures, and enhance security all at once.
Why zero trust?
Technological advancements and workforce transformations have dissolved the traditional security perimeter. The movement of critical assets to the cloud and the rise of telework mean ever-expanding perimeters for federal agencies to defend. Transitioning to a zero trust architecture improves security posture, enables continuity of operations, and augments digital transformation.
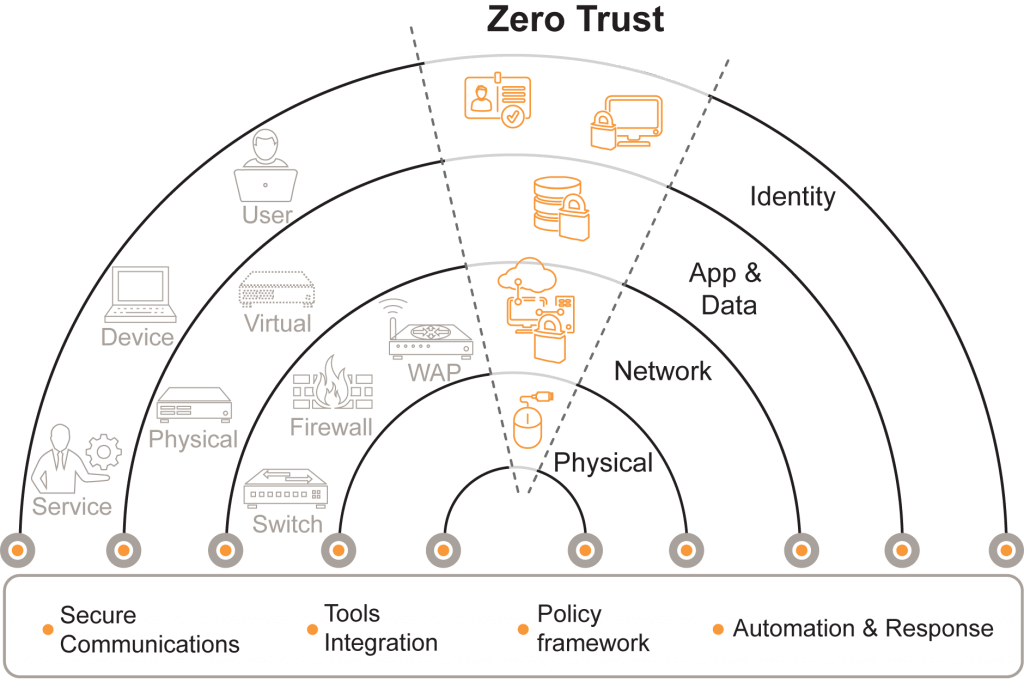
Zero Trust Core Tenets
Under a zero trust framework, all network traffic is untrusted and always verified. Comprehensive zero trust models apply fundamental security principles to all endpoints, applications, and user identities. At Merlin, we follow five core tenets for the successful application of zero trust. Following these tenets ensures that effective security design principles exist at every layer of the IT stack.
Steps Agencies Can Take Today
Blog Post: How to future-proof your technology stimulus spending
The CARES Act passed in March provides agencies with funding that can help address telework infrastructure and security needs. Agencies can use the funds to modernize and move towards embracing a zero trust architecture by following some key principles. Read more.
Additional Insights on Securing Remote Workers
Supporting remote workers is the number one priority for most federal agencies today. Legacy remote access systems were not designed to secure the remote worker, protect the endpoints, and to remotely access applications. Learn how to harness the cloud for the rapid surge of telework and IT services while scaling and adapting for the future.









