ATARC | Scenario 6-10
Protect on-premise and cloud systems against active exploits and data exfiltration
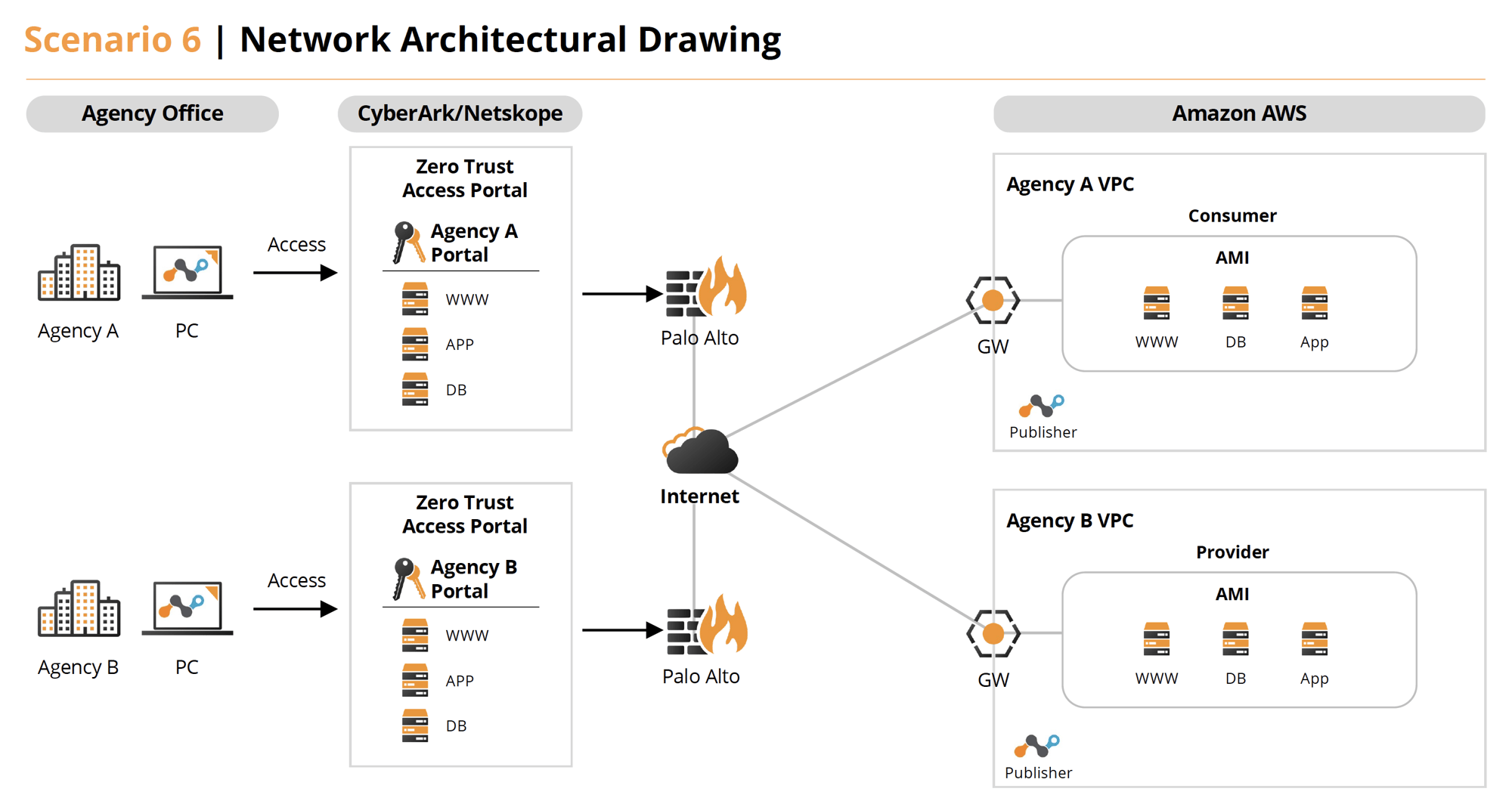
Scenario 6
An agency system interfaces with another agency’s system (e.g. accessing fingerprint information as part of a background investigation process). Both systems are public cloud-based. Describe both normal, ongoing operations and an incident when the agency is informed the other agency’s system is experiencing an active exploit.
Solution 6
- Under normal operations Agency A (AWS) has a web app that access images and a database from Agency B (AWS). These host both have Netskope (DLP and more) and CrowdStrike (EDR and CPSM) agents on them. They also utilize Illumio for Micro Segmentation to further secure the network protocols required. The staff accesses all components the via Cyolo (ZTNA) providing VPN-less, secure access with session recording.
- If an exploit is detected by the tools or by an analyst, they can utilize case management tools in Swimlane to investigate and resolve issues. Swimlane provides the benefit of integrating workflows between Netskope, CrowdStrike, Illumio, Splunk (SIEM) and Jira Service Desk (ITSM) during problem resolution. Cyolo can also provide session replays of user access.
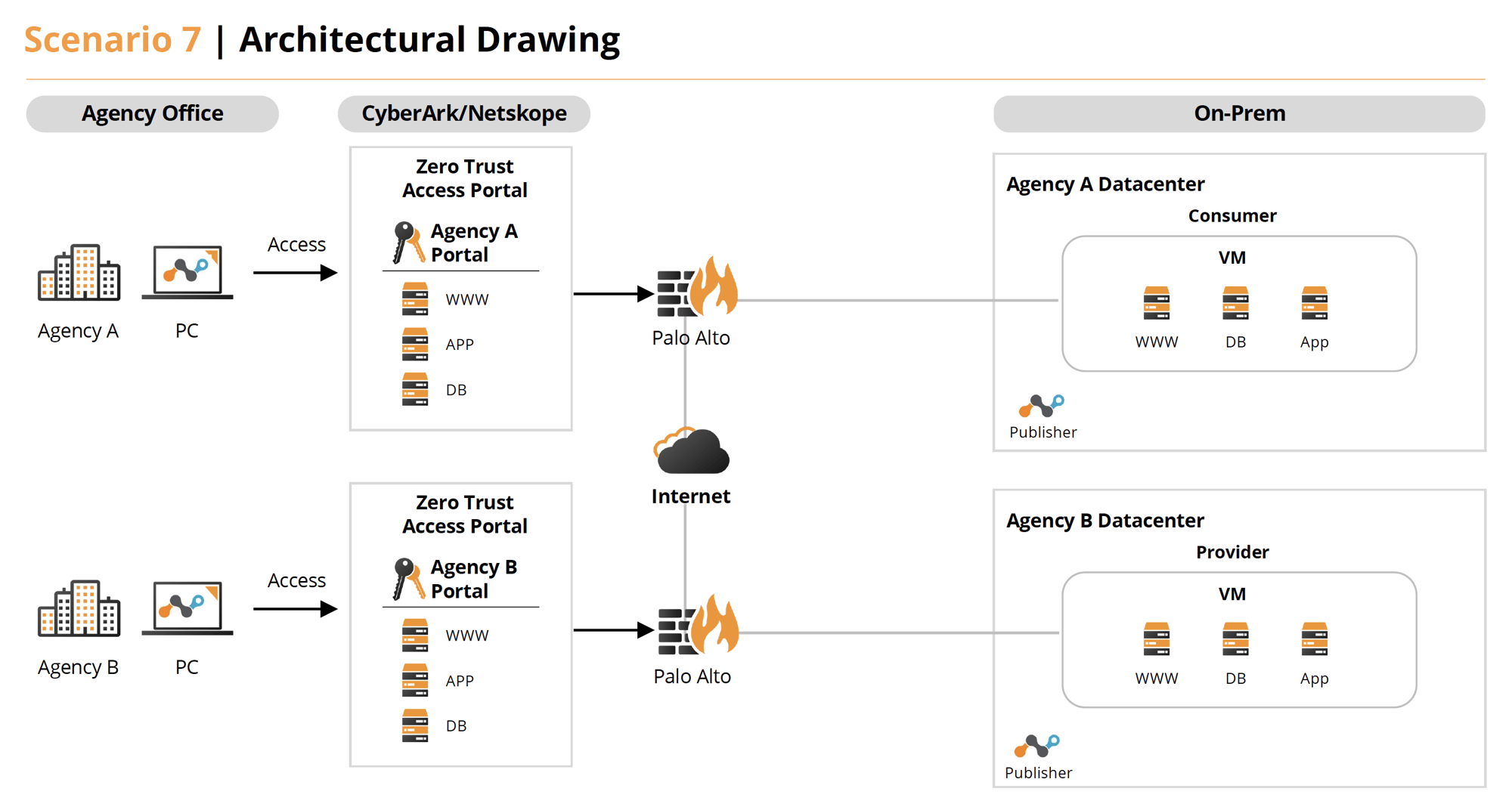
Scenario 7
Use the conditions described in Scenario 6 but both systems are located on-premise in the agencies’ data centers.
Solution 7
- Under normal operations Agency A (On-Prem) has a web app that access images and a database from Agency B (On-Prem). These host both have Netskope (DLP and more) and CrowdStrike (EDR , FileVantage) agents on them. They also utilize Illumio for Micro Segmentation to further secure the network protocols required. The staff accesses all components the via Cyolo (ZTNA) providing VPN-less, secure access with session recording.
- If an exploit is detected by the tools or by an analyst, they can utilize case management tools in Swimlane to investigate and resolve issues. Swimlane provides the benefit of integrating workflows between Netskope, CrowdStrike, Illumio, Splunk (SIEM) and Jira Service Desk (ITSM) during problem resolution. Cyolo can also provide session replays of user access.
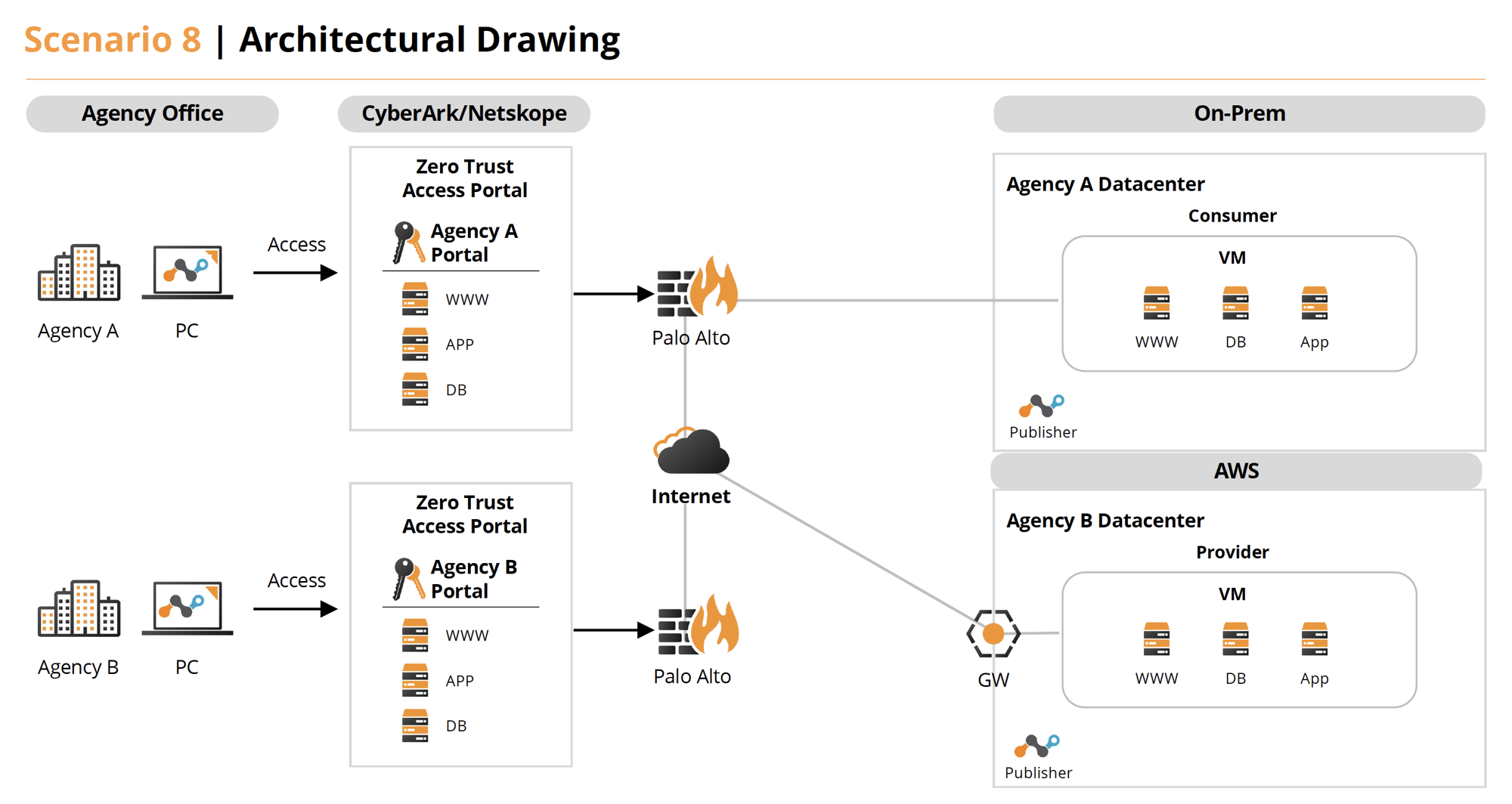
Scenario 8
Use the conditions described in Scenario 6 but the primary system is located on-premise in the agencies’ data centers and the secondary, accessed system is in a public cloud.
Solution 8
- Under normal operations Agency A (On-Prem) has a web app that access images and a database from Agency B (AWS). These host both have Netskope (DLP and more) and CrowdStrike (EDR , FileVantage, CPSM) agents on them. They also utilize Illumio for Micro Segmentation to further secure the network protocols required. The staff accesses all components the via Cyolo (ZTNA) providing VPN-less, secure access with session recording.
- If an exploit is detected by the tools or by an analyst, they can utilize case management tools in Swimlane to investigate and resolve issues. Swimlane provides the benefit of integrating workflows between Netskope, CrowdStrike, Illumio, Splunk (SIEM) and Jira Service Desk (ITSM) during problem resolution. Cyolo can also provide session replays of user access.
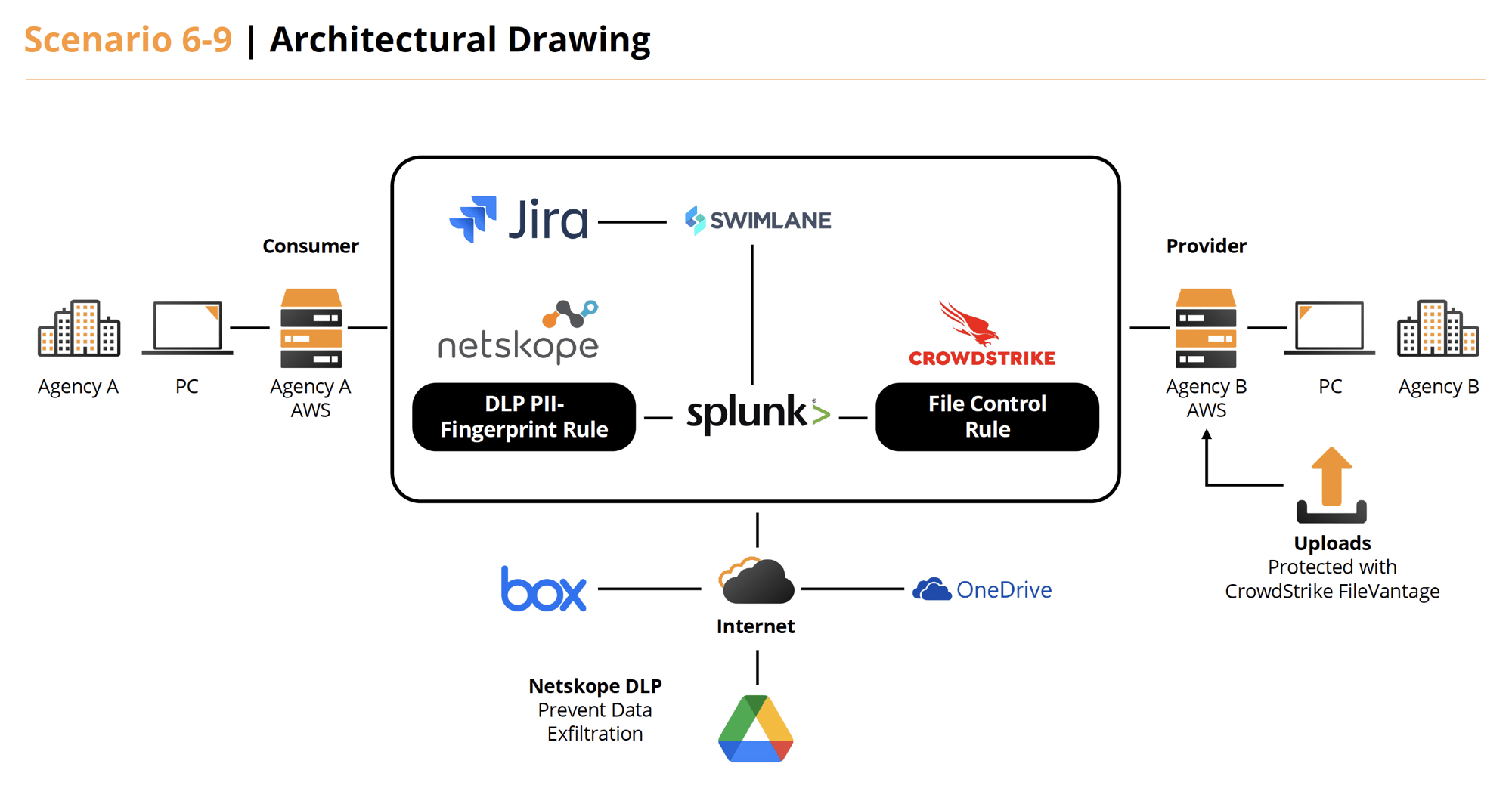
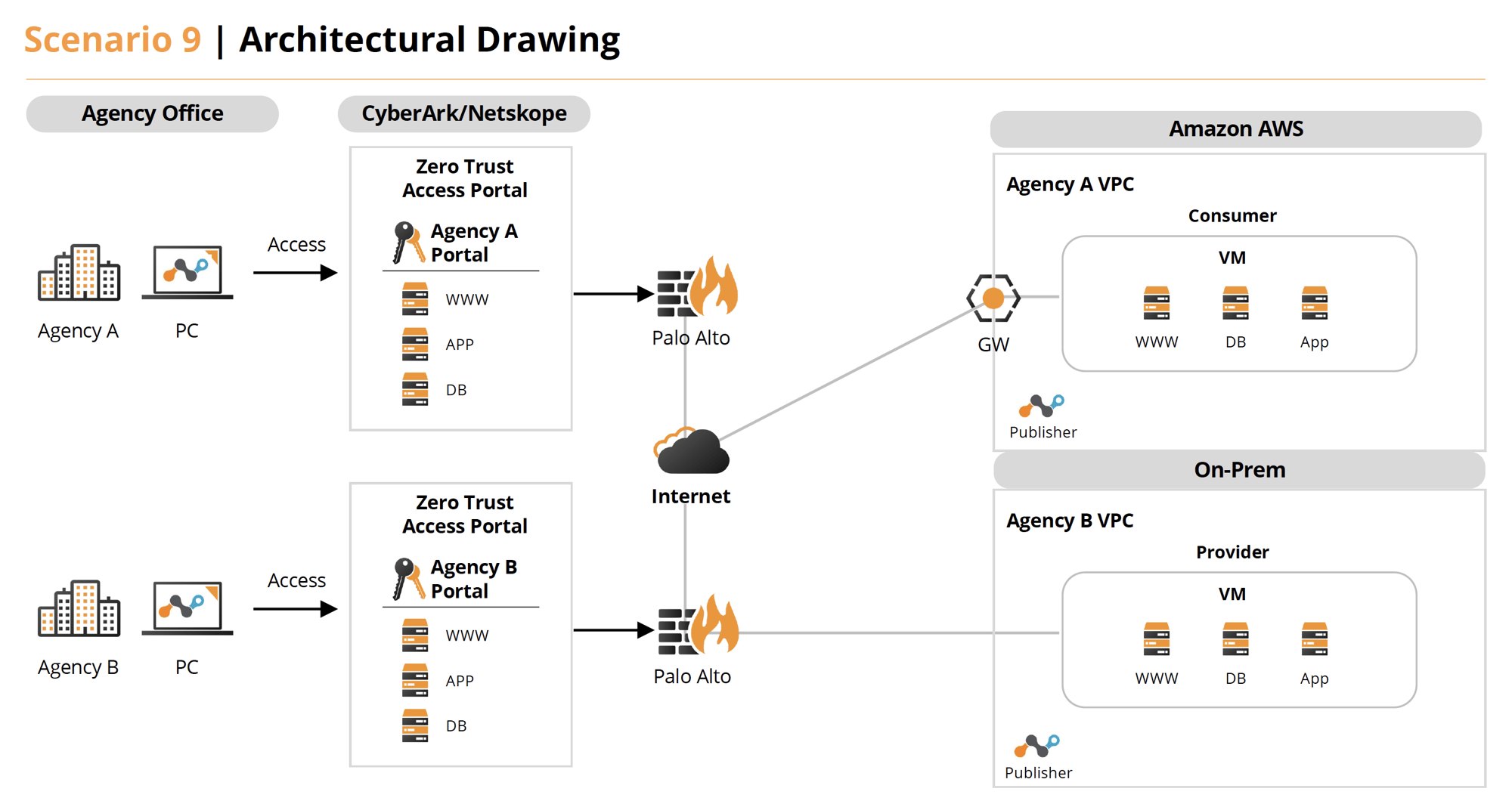
Scenario 9
Use the conditions described in Scenario 6 above but the primary system is housed in a public cloud and the secondary, accessed system is located on-premise in the agency’s data center.
Solution 9
- Under normal operations Agency A (AWS) has a web app that access images and a database from Agency B (On-Prem). These host both have Netskope (DLP and more) and CrowdStrike (EDR, FileVantage, CPSM) agents on them. They also utilize Illumio for Micro Segmentation to further secure the network protocols required. The staff accesses all components the via Cyolo (ZTNA) providing VPN-less, secure access with session recording.
- If an exploit is detected by the tools or by an analyst, they can utilize case management tools in Swimlane to investigate and resolve issues. Swimlane provides the benefit of integrating workflows between Netskope, CrowdStrike, Illumio, Splunk (SIEM) and Jira Service Desk (ITSM) during problem resolution. Cyolo can also provide session replays of user access.
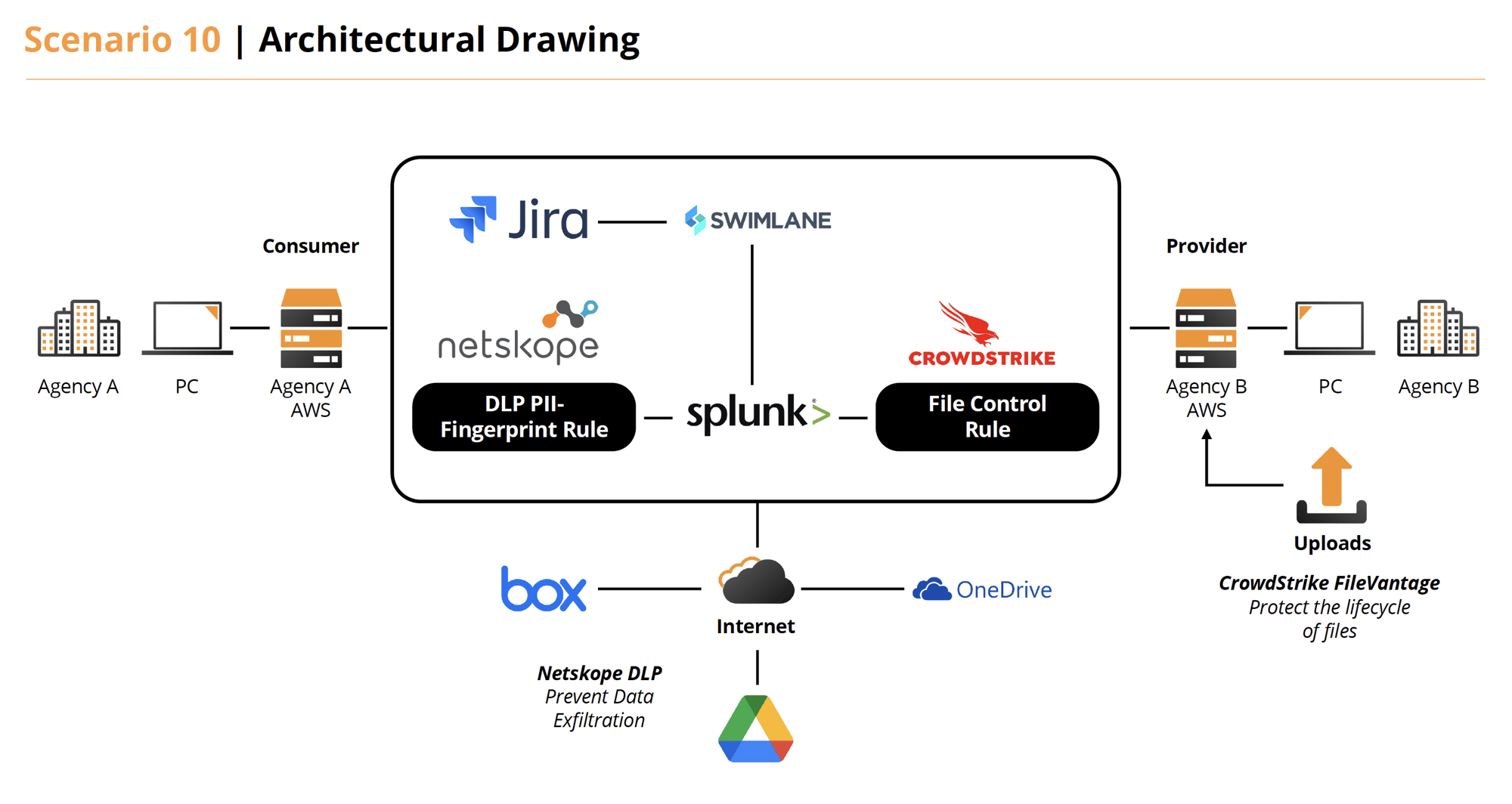
Scenario 10
Use Scenarios 6 through 8 above but address from the perspective the primary agency system is being accessed to gain fingerprint data (PII or High Categorized) by another agency’s system.
Solution 10
- Overall: File protection is built into all the Scenarios presented in 6 – 10. The web servers on-prem and on AWS are monitoring the ingestion and movement of uploaded fingerprint files. The files are classified as PII by the “ATRAC PII” policy.
- CrowdStrike: File Vantage provides monitoring of files being accessed on endpoints. It can provide tiering of alerts based on user actions. These alerts can then drive automation via email, forwarded alerts, and SIEM logging. These alerts can also drive remediation activities as well.
- Netskope: Netskope DLP provides the ability to protect the movement of files based on categorization on on-prem and cloud endpoints. For example, the SaaS app Google Drive is configured to not allow the movement of PII files to or from it.
- Splunk: Splunk provides an integration with Netskope to provide useful information regarding alerts received.
- Swimlane: Playbooks are defined to handle DLP/PII-related events and others. Here we automate and orchestrate the flow of the registration of an alert to taking action by collecting information and creating a service ticket to work issue.