Scenario
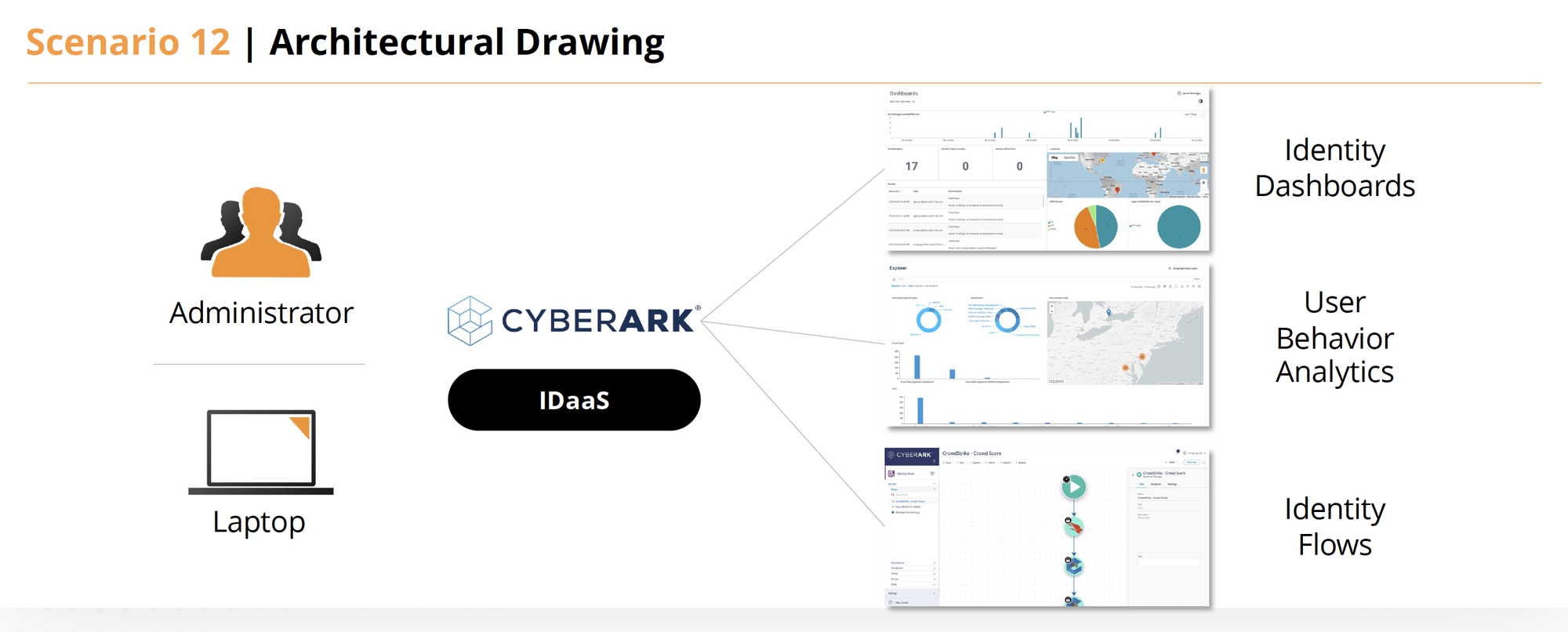
The ICAM administrator has reported a user's credentials were compromised. Describe any tools/methods you provide to validate unauthorized access to systems under the ZTA umbrella has not occurred, either on-premise or cloud-based.
Solution
-
CyberArk Identity can be used to determine if any unauthorized access to systems has occurred, as in our solution, we are using it as the primary authentication and authorization point based on multiple login factors. – Username, Password, Yubikey, geographical location, along with other factors to determine user risk.