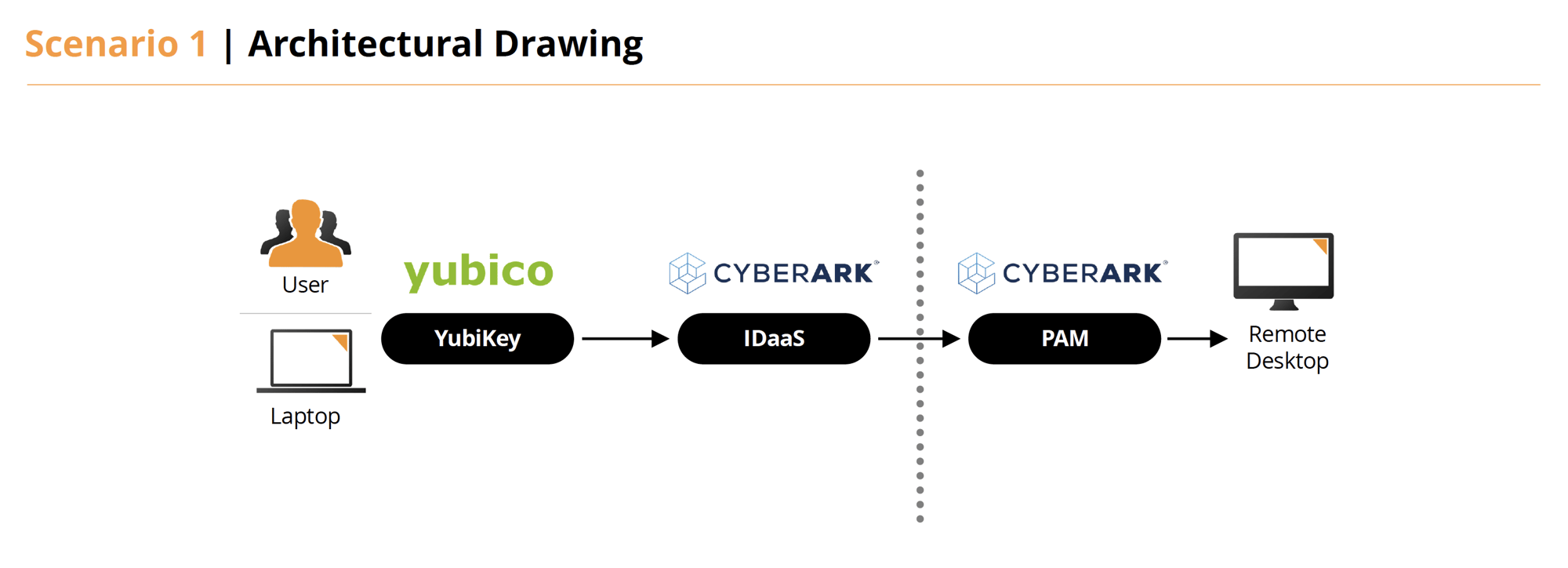
ATARC | Scenario 1
Secure access with MFA and Privileged Access Management from personally owned devices
Scenario
An agency employee is working remotely, using personally owned devices, must regularly access a public cloud based, agency application. The employee routinely accesses the system as a standard user but occasionally switches to administrator mode to perform systems maintenance. The user’s physical location changes frequently with personal travel. At times, that travel takes the user to countries designated as a high threat due to state-sponsored cyber activity. Beyond standard user and administrator activity, there is a specific instance when the user is using administrator privileges to troubleshoot an issue and accesses another system. Further into the troubleshooting process, the user attempts to access a third system but does not have administrator privileges.
Solution
- Using the person’s personally owned device, the user would connect to the CyberArk Identity portal using their username and password and a YubiKey.
- Using CyberArk Identity, we can manage user geographic location and implement policies to block or allow.
- While authenticated with CyberArk Identity and within Five Eyes (FVEY), the user would have access to All applications, including CyberArk PAM (PVWA). While they are not within FVEYs, they only have no access.
Reference : The Five Eyes (FVEY) is an intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States.