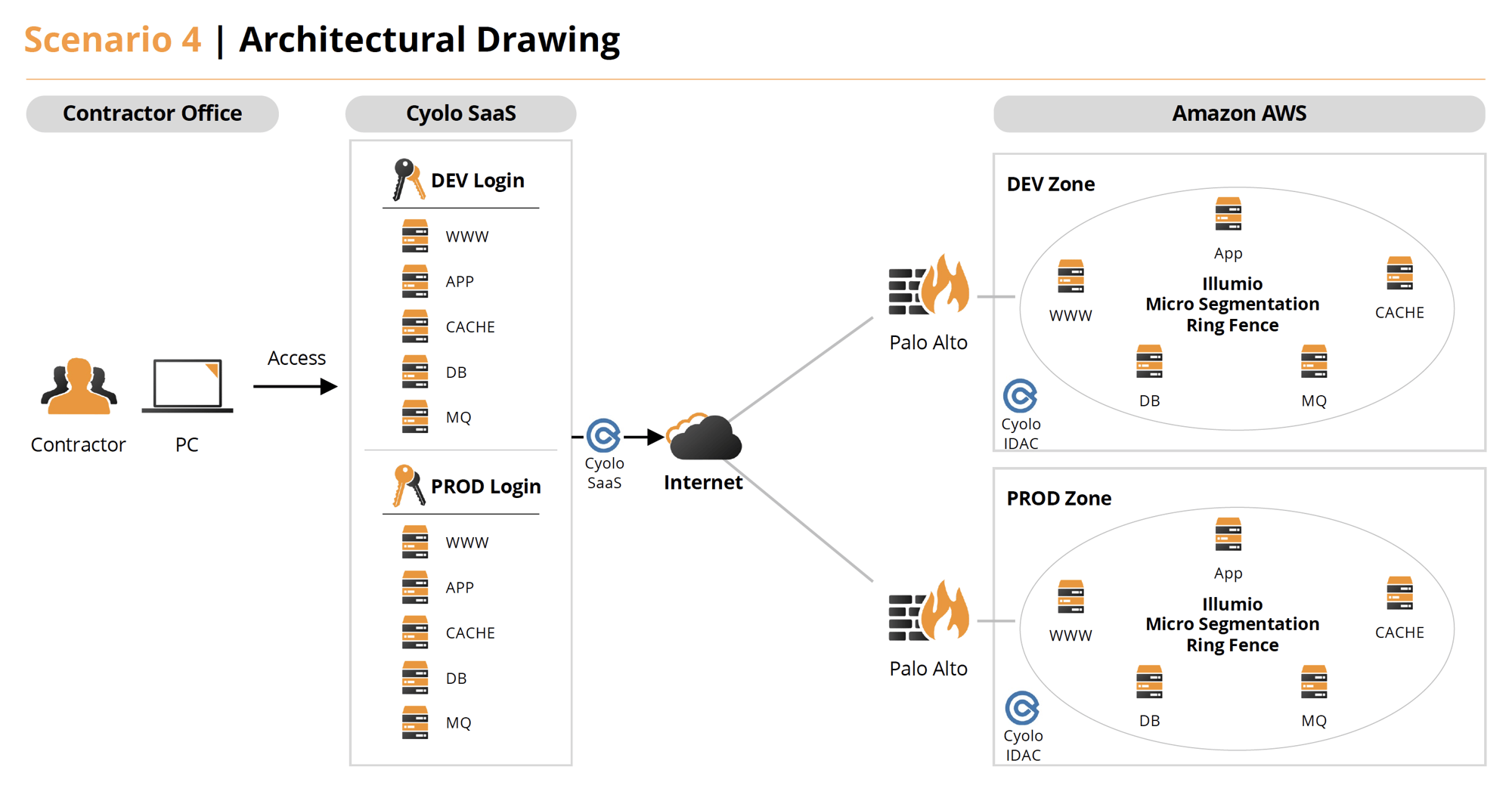
Scenario 3
A contracted employee provides ongoing improvements to an agency system as part of a development team and provides administrator and routine maintenance to the operational system. Development is performed from the contracted employee’s corporate offices using devices provides by his/her company. Development is performed on a separate network, isolated from the production network. Both operate within a data center located at the agency’s facilities. When appropriate, the contracted employee moves systems from the development environment into production.
Solution 3
- A contracted employee logs into the Zero Trust Access portal (Cyolo) as a Development persona.
- They can only access the Development systems they have been provided access to by Cyolo.
- The Development and Production systems are separated via macro-segmentation being provided by the firewalls (Palo Alto). The components of the application are further protected via Micro-Segmentation (Illumio) to prevent unauthorized lateral communications and to prevent Dev to Prod bleed-over in case of misconfigurations.
- All endpoints are protected with CrowdStrike EDR to allow control of host and to provide containment in the event of a breach.
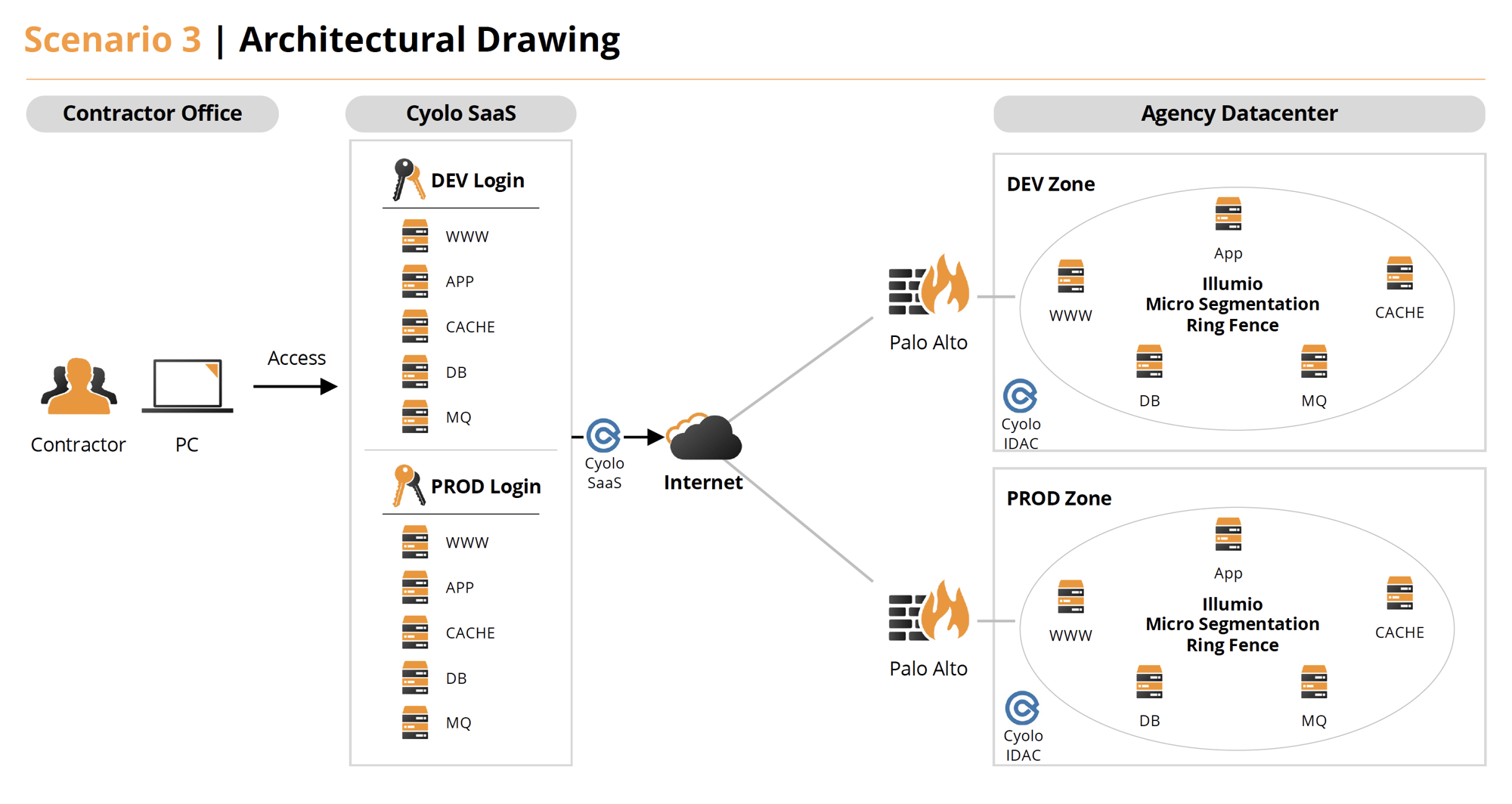
Scenario 4
Use the conditions described in Scenario 3 above but both the development and production systems are cloud-based.
Solution 4
- A contracted employee logs into the Zero Trust Access portal (Cyolo - SaaS) as a Development persona.
- They can only access the Development systems they have been provided access to by Cyolo.
- The Development and Production systems are separated via VLAN Segmentation being provided by the Subnets in the VPC.
- The components of the application are further protected via Micro-Segmentation (Illumio) to prevent unauthorized lateral communications and to prevent Dev to Prod bleed-over in case of misconfigurations.
- All endpoints are protected with CrowdStrike EDR to allow control of host and to provide containment in the event of a breach.
- It is important to note that just because these are cloud workloads, we can still leverage the same tool set.